Agenda:
- Intro
- Nmap Scripting Engine (NSE)
- NSE Categories
- Nmap banner grabbing
- Conclusion
- Related articles
Nmap Scripting Engine
Nmap Scripting Engine (NSE) allows users to integrate scripts to the scan process to execute additional tasks. While we can get scripts from Nmap itself we can also write our own scripts. Depending on the script, tasks may be executed during or after the scan process (post scan scripts). The NSE scripts are divided into categories according to their functionalities.
Syntax: when using scripts with our scans we need to specify –script=<scriptname>, for this tutorial I will use the following script: –script=banner
NSE Categories:
auth: this category contains scripts related to authentication processes. An example is the ssh-auth-methods script to detect the authentication method of a ssh service.
brute: this category contains scripts to carry out brute force attacks.
broadcast: this category contains scripts to sniff packages within a network. For example the script broadcast-dropbox-listener can be used to sniff data from packages generated by Dropbox clients.
default: Default scripts.
Discovery: this category includes scripts used to discover hosts and services.
DOS: This category includes scripts to carry out denial of service attacks, or vulnerability tests, for example the script smb-vuln-ms10-054 will check if the system is vulnerable to a corruption memory bug which may cause a denial of service.
Exploit: this category includes scripts capable to exploit vulnerabilities on the target.
External: this category includes scripts which allow to add third party databases to our scan. The script hostmap-bfk which integrates a database with information on hosts pointing to the target.
Fuzzer: This category includes only 3 scripts to test fuzzing attacks. The scripts are dns-fuzz
To test DNS servers vulnerable to fuzzing attacks. The script http-form-fuzzer tests websites for fuzzing vulnerabilities while the script http-phpself-xss checks for XSS vulnerabilities.
Intrusive: The intrusive category includes a variety of scripts
Malware: this scripts checks for malware infections on targets.
Safe: This category includes non-offensive scripts which won’t crash services.
Version: this category contains script to detect versions of services, hardware among more. The script hnap-info is an example of a Version script used to gather information on the target’s hardware.
Vuln: this category includes scripts to find specific vulnerabilities on targets.
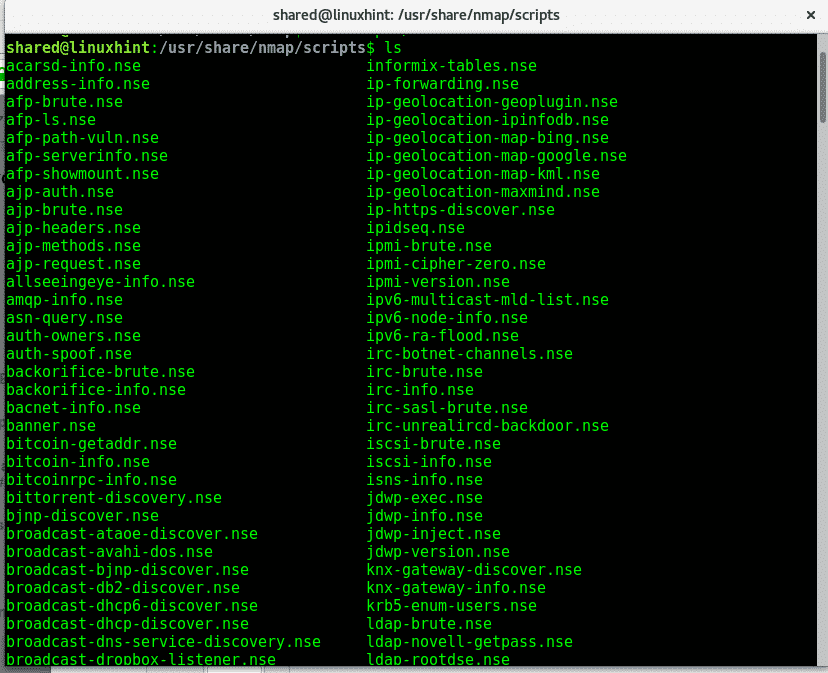
Note: Nmap scripts are located in the directory /usr/share/nmap/scripts
Nmap Banner Grab
Banner grabbing mainly consists on sending requests to services in order to get responses which will allow us to learn their versions, it may be considered part of the OS and version detection process to know our target’s software and it’s possible vulnerabilities for future exploitation. An example of basic scan using nmap would be the following:

As you can see nmap informs it is a web server with ports 80 and 443 available, other ports are filtered.
Using the option -sV we can instruct nmap to check for service versions, we can define the check aggressivity defining the level from 0 to 5. While 5 is more aggressive the lighter banner grab is faster.
Note: –version-intensity 5 should not be considered as banner grab, banner grabbing is done by reading the service banners, information sent by listening services while –version-intensity 5 includes additional, and more aggressive techniques.
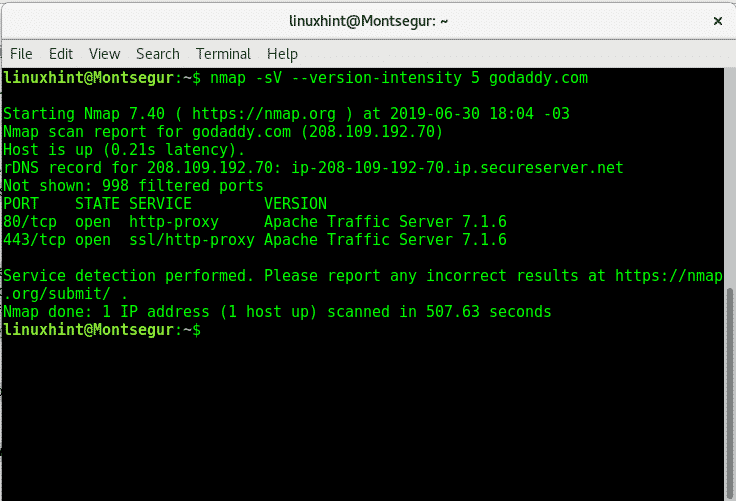
After including the -sV option nmap reveals the server is running the proxy reverse Apache Traffic Server 7.1.6. In this case Goddady kept it’s software updated, but after getting our target’s software versions we can look for exploits at databases like https://www.cvedetails.com/vulnerability-list/vendor_id-45/product_id-19990/Apache-Traffic-Server.html
Let’s try the same scan against a server offering more services:
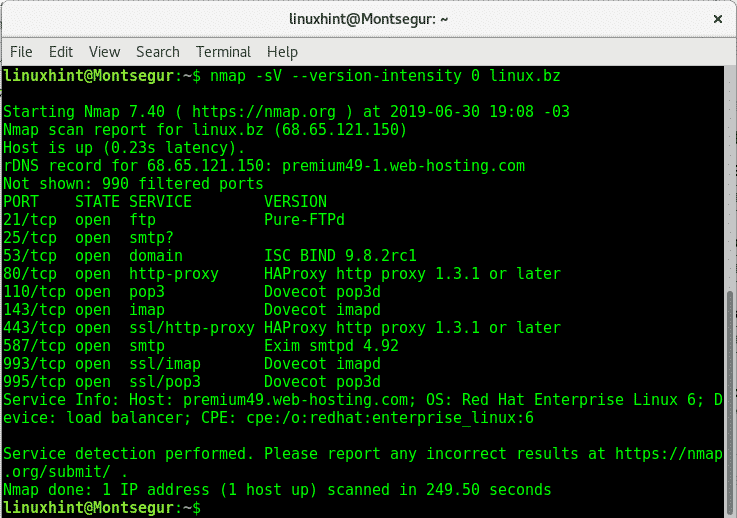
Nmap shows all available services at the server including their versions and the operating system Red Hat Enterprise Linux.
Now let’s incorporate the banner script from the NSE suite:

Where:
nmap: calls the program
-sV: Version detection.
–script=: instructs nmap to incorporate a NSE script.
banner: After “–script=” we define the script, in this case banner.
Closer screenshot:
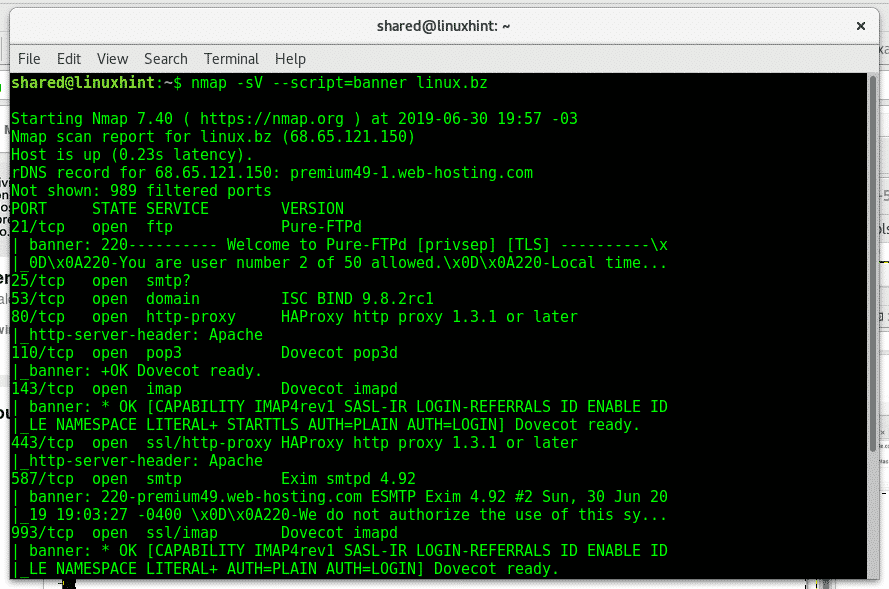
Additional information provided by the banner scripts include from authentication to protocol reports.
In the following sample I will scan the port 21 of linux.bz trying to get information on the FTP server using the banner script:

Where:
nmap: calls the program
-p 21: specifies the port 21 only.
-sV: version detection
–script=: instructs nmap to incorporate a NSE script.
banner: After “–script=” we define the script, in this case banner.
The output reveals the server is using Pure-FTP, it even reveals the maximum allowed limit of users (up to 50).
Now let’s try the banner script to check LinuxHint ssh port:
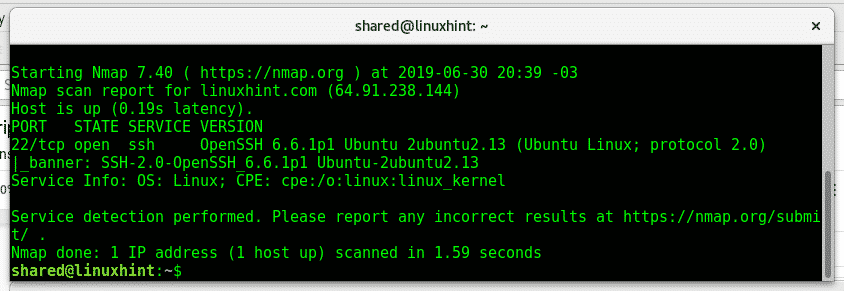
Nmap reveals linuxhint uses OpenSSH 6.6.1 and Ubuntu Linux.
Conclusion:
Banner grabbing is a formidable way for sysadmins to gather information on their devices and running software. It may be helpful to detect vulnerable versions of specific software or services to patch or update. It’s main obstacle is the time the scan process may take. NSE banner script by default takes 5 seconds per port. This technique would be optimized if the user specifies nmap what ports to audit.
I hope you found this tutorial helpful as introduction to nmap NSE and nmap grabbing techniques. Keep following LinuxHint for more updates and tips on Linux. Before any inquiry on Linux or networking don’t hesitate to contact us through our support channel https://support.linuxhint.com.
Related articles:
Nmap flags and what they do
Nmap ping sweep
How to scan for services and vulnerabilities with Nmap
Nessus Ubuntu Installation and Tutorial
OpenVAS Ubuntu Installation and Tutorial
Getting started with Nikto vulnerability scanner
Installing Nexpose Vulnerability Scanner on Debian/Ubuntu