Nmap “ping sweep” is a method to discover connected devices in a network using the nmap security scanner, for a device to be discovered we only need it to be turned on and connected to the network. We can tell nmap to discover all devices in the network or define ranges. In contrast to other types of scanning ping sweep is not an aggressive scan as these we previously explained on LinuxHint to scan for services and vulnerabilities using nmap, for ping sweep we can skip some of nmap’s regular stages in order to discover hosts only and make harder for the target to detect the scan.
Note: replace the IP addresses 172.31.x.x used for this tutorial for some belonging to your network and the network device enp2s0 for yours.
Getting started with ping sweep
First of all let’s know about our network by typing ifconfig:

Now let’s say we want to discover all hosts available after 172.31.X.X, nmap allows us to define IP ranges and to define sub ranges within each octet. For this we’ll use nmap’s old flag (parameter) -sP, the parameter is still useful but was replaced for -sn which will be explained later.
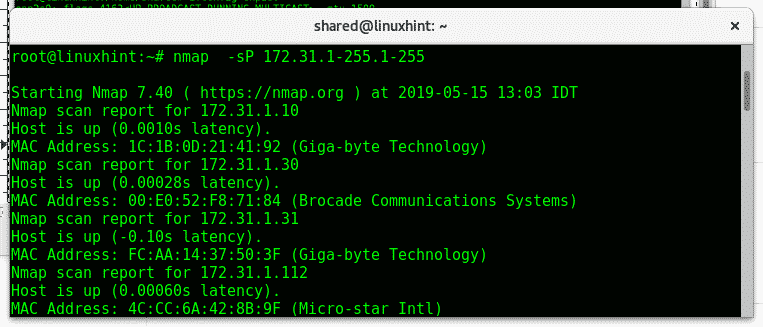
Where:
Nmap: calls the program
-sP: tells nmap no to do a port scan after host discovery.
As you can see nmap returns the available hosts and their IP and MAC addresses but no information on ports.
We can also try it with the last octet:
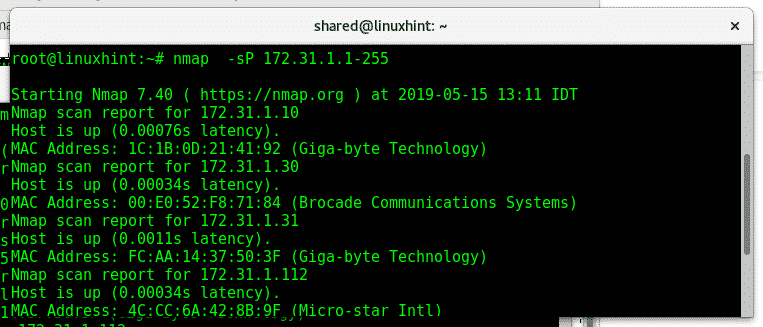
The flag -sn (No port scan) replaces the -sP you just tried.
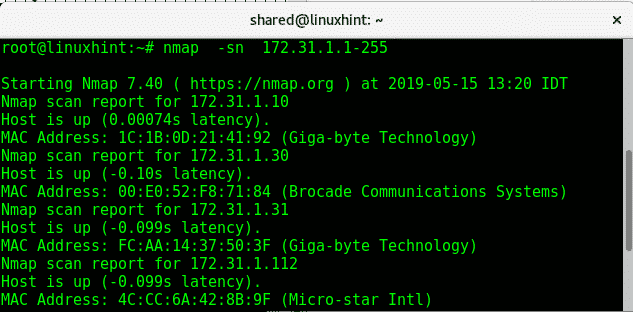
As you can see the output is similar to the previous scan, no information on ports.
The parameter -Pn (no ping) will scan ports of the network or provided range without checking if the device is online, it wont ping and won’t wait for replies. This shouldn’t be called ping sweep but it is useful to discover hosts, In the terminal type:
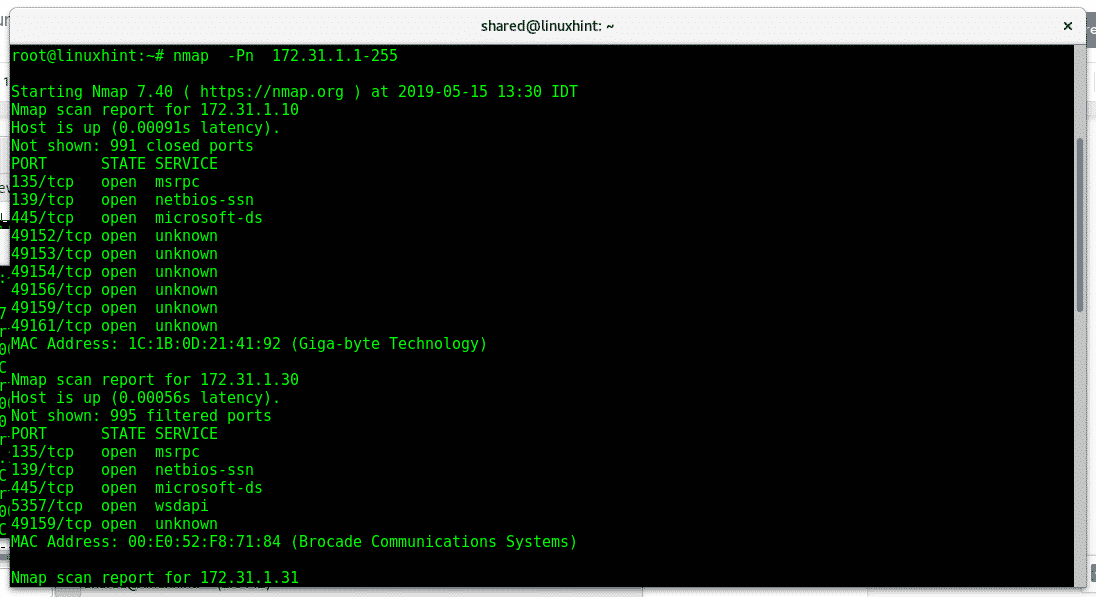
Note: if you want nmap to scan the whole range of an octet you can replace 1-255 for wildcard (*).
The parameter -sL (List scan) is the less offensive one, it enumerates the IP addresses in the network and tries to resolve through reverse-DNS lookup (resolve from ip to host) to know the hosts are there. This command is useful to print a list of hosts, In the terminal type:
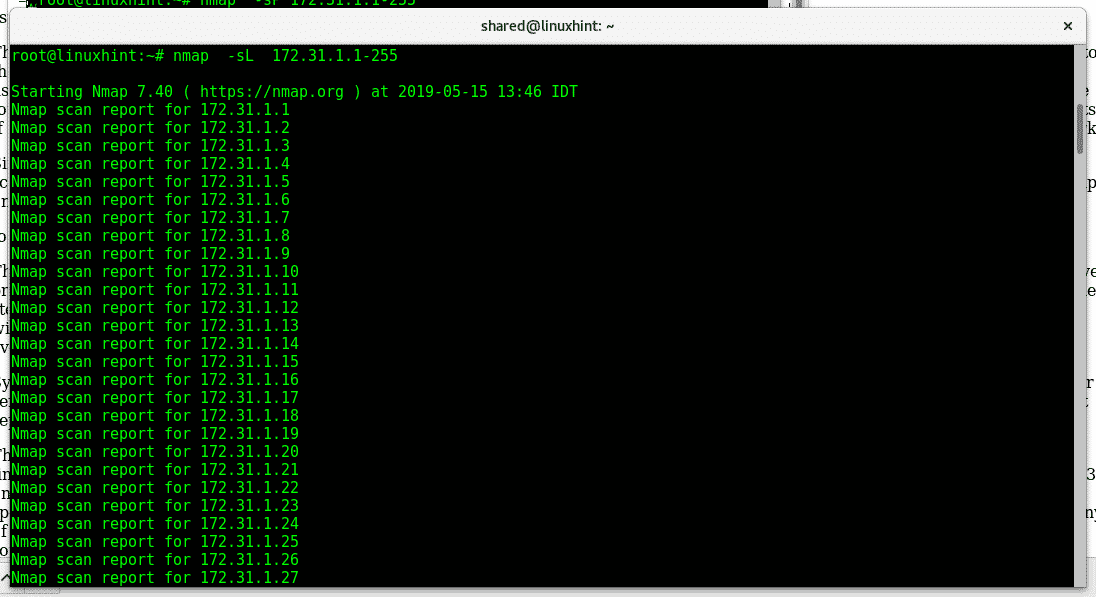
Now let’s assume we want to scan the whole network with NO PORT SCAN excluding a specific device, run:
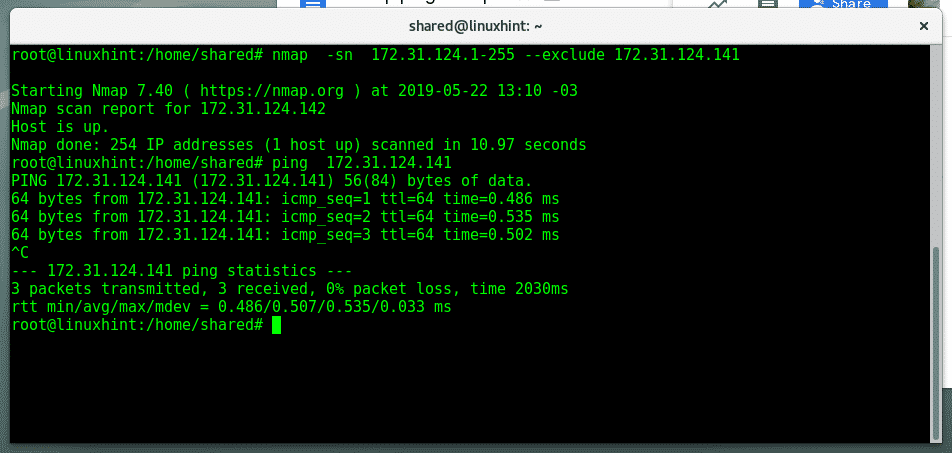
In this network we have only two devices with IP 172.31.124.X, nmap scanned the whole network finding only one and excluding the second according to the passed instruction –exclude. As you see with the ping response the IP 172.31.124.142 is available despite being undetected by nmap.
Some of the flags explained above can be combined with flags explained in the previous tutorial. Since ping sweep is a non-offensive discovery tool, not all flags can be combined since flags used for footprinting depend or more offensive scan flags.
The next tutorial of this series will focus on network scan and we will combine some flags in order to try to cover offensive scans, for example, sending fragmented packets to avoid firewalls using the flag -f formerly explained.
I hope this tutorial was useful as an introduction to ping sweep, for more information on Nmap type “man nmap”, should you have any inquiry contact us opening a ticket support at LinuxHint Support. Keep following LinuxHint for more tips and updates on Linux.