Previous brief introduction to nmap’s target syntax:
When we use nmap we first call the program “nmap”, then specify the instructions through flags (like the port with the flag -p) and the target/s using it’s IP, host or host range. While there are many ways to pass targets we’ll use 5: single ip scan which you can execute by providing nmap the target’s host or IP, IP range scan which you can define by using a hyphen between the starting and end point of possible IPs between 0 and 255 (e.g 192.168.1.35-120 which instructs nmap to scan between IP 35 and 120 of the last octet), multiple target scan which we’ll carry out importing targets from a file, random scan and full octet’s scan by using wildcard (*).
Examples:
Single IP scan: nmap X.X.X.X/www.hostname.com
IP range scan: nmap nmap X.X.X.Y-Z/X.X.Y-Z.Y-Z
Random scan: nmap -iR X <FLAG>
Full octet scan: X.X.X.*
Where: X,Y and Z are replaced by numbers
Previous brief introduction to nmap’s port states:
Nmap outputs report between 6 possible states when scanning ports:
Open: the port is open and an application is listening through it.
Closed: the port is closed, not application is listening.
Filtered: a firewall prevents nmap from reaching the port.
Unfiltered: Port is accessible but nmap is unable to check it’s state.
Open|filtered: Nmap is unable to determine if a port is open or filtered.
Closed|Filtered: Nmap is unable to determine if a port is closed or filtered.
Nmap flags
Nmap flags are the parameters we use after calling the program, for example -Pn (no ping) is the flag or parameter to prevent nmap from pinging targets. Below you’ll find nmap’s main flags with examples.
-p: the -p flag or parameter is useful to specify one or many ports or port ranges. We can add several ports separated by a comma as shown in the image below:
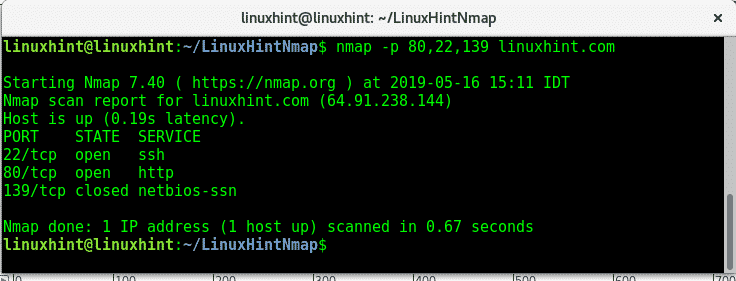
I instructed nmap to scan LinuxHint’s server for ports 80,22,139, while http and ssh are open netbios port is closed.
To scan a port range you can use a hyphen to separate the range’s limit, to scan LinuxHint’s ports from the 21 to 25 run:

Optionally you can also define ports by their default service name rather than their port number like “nmap -p ssh <target>”
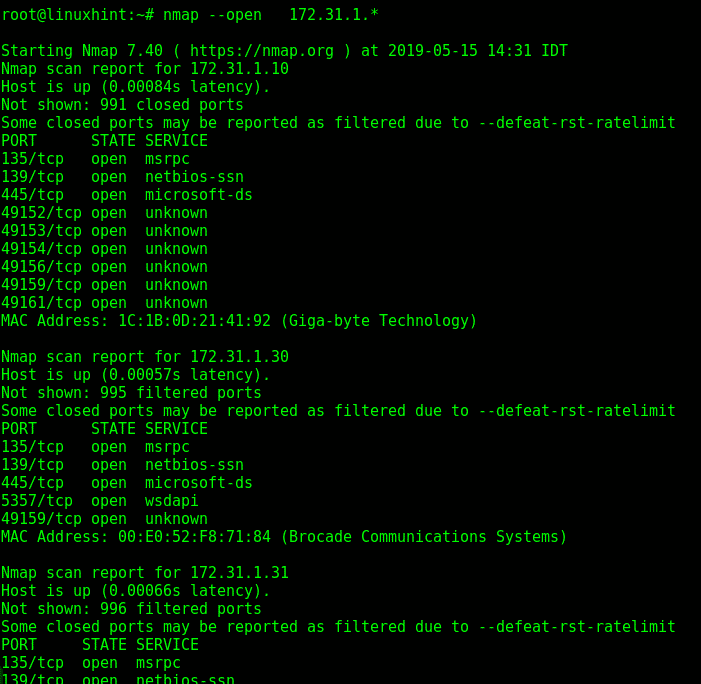
–open: This flag instructs nmap to find open ports on a specified IP range, in this example nmap will look for all open ports of IP addresses within the range 172.31.1.1-255 (using wildcard equals using the 1-255 range.)
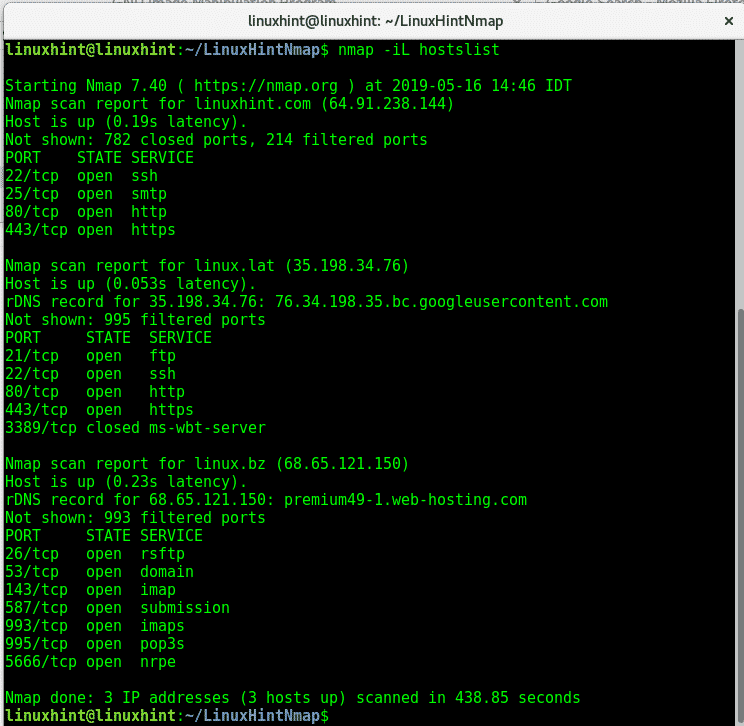
-iL: Another way to define targets by creating a targets list. In the list hosts can be separated by comma, space, tab or new line. Below an example of nmap used to scan multiple targets using a list called “hostslist” which includes LinuxHint and other two hosts.
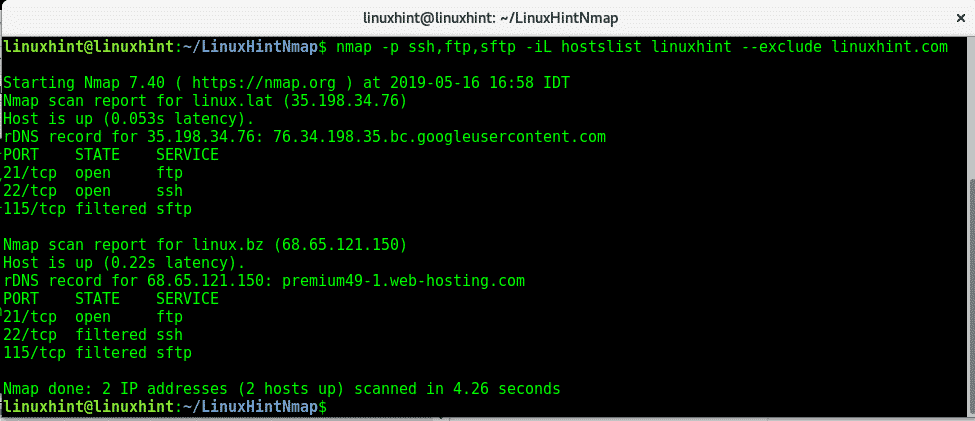
–exclude: This flag is useful to exclude IP addresses or hosts from scans when we scan IP ranges or target files. In the following example I’ll use the hostlist again to scan ports ssh, ftp and sftp but I instruct nmap to exclude linuxhint.com from the list. As you see in contrast with the result shown in the -iL flag example linuxhint.com wasn’t scanned.
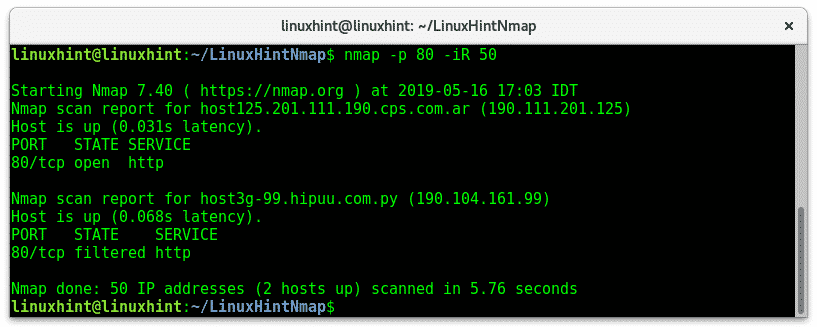
-iR: The -iR flag instructs nmap to find hosts randomly, the -iR flag depends on an argument and a numerical instructions, it requires the user to define how many hosts or targets nmap should generate. In the following example I apply the -iR flag to scan http ports of 50 automatically generated random addresses, from the generated addresses nmap found 2 up hosts.
In the following example I instruct nmap to generate 200 random targets to scan for the NetBios port.

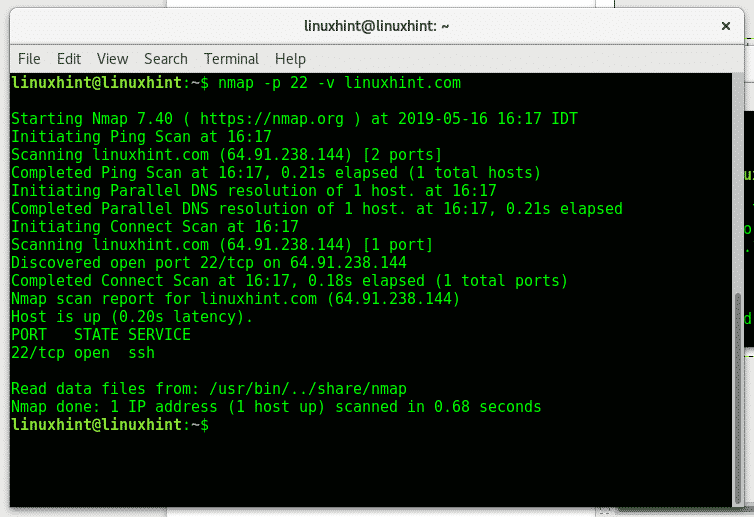
-v: The -v flag (verbosity) will print information on the scan process. By default nmap doesn’t show the process, this parameter will instruct nmap to show what’s going on during the scan.
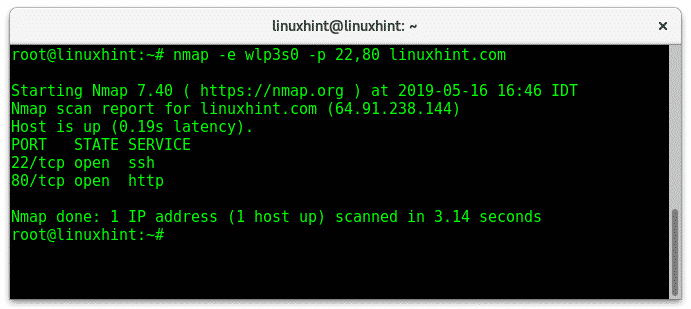
-e: This flag allows us to specify a network interface (e.g eth0, wlan0, enp2s0,etc), useful if we are connected both through our wired and wireless cards. In my case my wireless card is wlp3s0, to instruct nmap to use that interface to scan ports 22 and 80 on LinuxHint.
-f: The -f (fragment packets) flag is also used to try to keep the scan process undetected by fragmenting the packets making harder for firewalls or IDS to detect the scan. This option isn’t compatible with all nmap features.
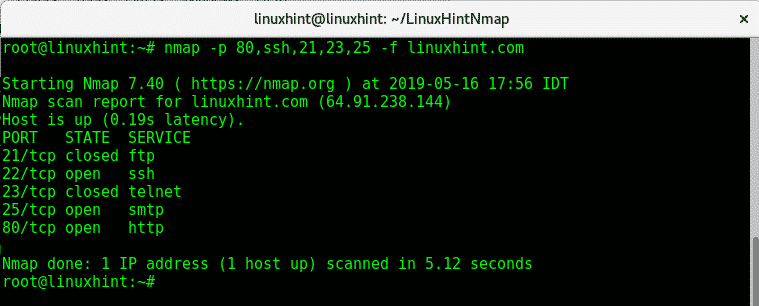
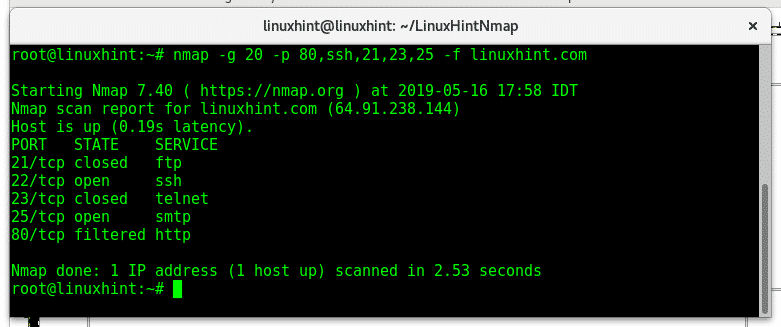
–source-port / -g: flags –source-port and -g are equivalent and instruct nmap to send packets through a specific port. This option is used to try to cheat firewalls whitelisting traffic from specific ports. The following example will scan the target from the port 20 to ports 80, 22, 21,23 and 25 sending fragmented packets to LinuxHint.
All flags mentioned above are the main flags used with nmap, the following tutorial on ping sweep explains additional flags for host discovery with a brief introduction to nmap’s phases.
For questions on nmap you can visit LinuxHint’s support center.