Different Ways to Secure SSH Server
All the configuration setting of SSH server can be done by modifying ssh_config file. This configuration file can be read by typing following command in Terminal.
NOTE: Before editing this file, You must have root privileges.
Now we discuss different ways to secure SSH server. Following are some methods we can apply to make our SSH server more secure
- By changing Default SSH Port
- Using Strong Password
- Using Public Key
- Allowing a single IP to Log in
- Disabling Empty Password
- Using Protocol 2 for SSH Server
- By Disabling X11 Forwarding
- Setting an Idle Timeout
- Setting a Limited Password Tries
Now we discuss all these methods one by one.
By Changing Default SSH Port
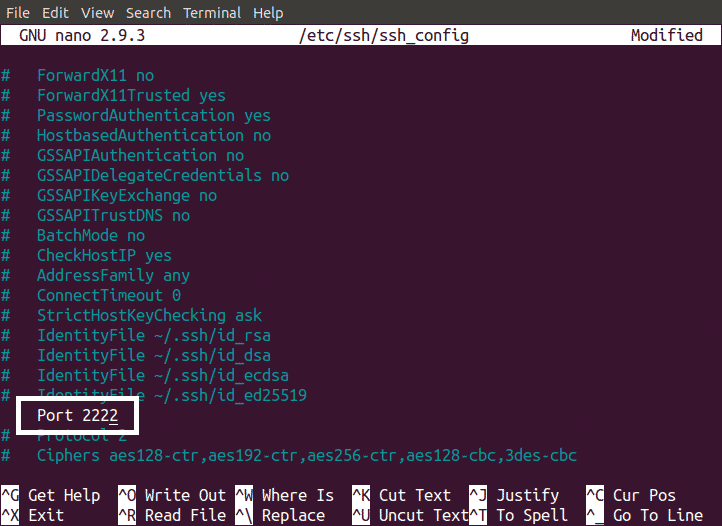
As described earlier, by default SSH uses Port 22 for communication. It is much easier for hackers to hack your data if they know which port is being used for communication. You can secure your server by changing default SSH port. To change the SSH port, open sshd_config file using nano editor by running the following command in Terminal.
Find the line in which port number is mentioned in this file and remove the # sign before “Port 22” and change the port number to your desired port and save the file.
Using Strong Password
Most of the Servers are hacked because of a weak password. A weak password is more likely to be hacked by hackers easily. A strong password can make your server more secure. Following are the tips for a strong password
- Use a combination of uppercase and lowercase letters
- Use numbers in your password
- Use lengthy password
- Use special characters in your password
- Never use your name or date of birth as password
Using Public Key to Secure SSH Server
We can login to our SSH server using two ways. One is using Password and the other one is using Public key. Using public key to login is much more secure than using a password to log into SSH server.
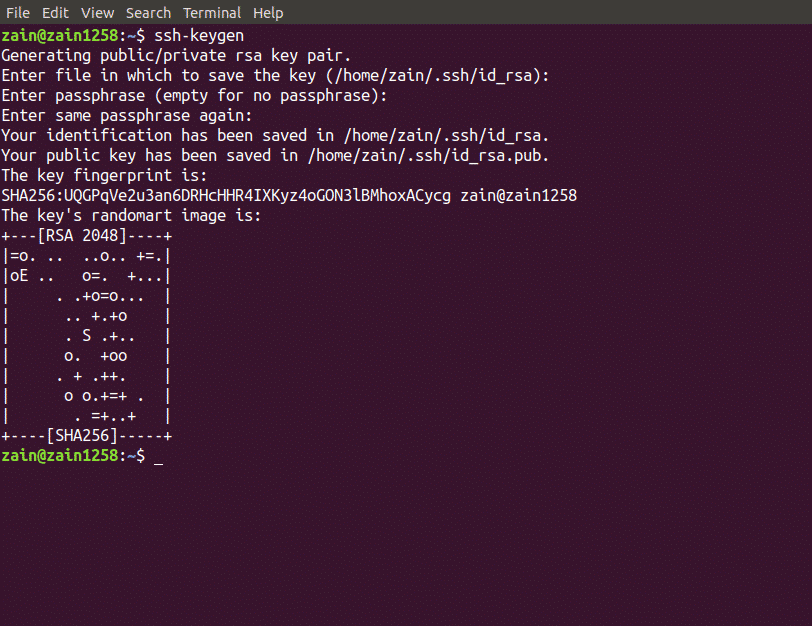
A key can be generated by running the following command in Terminal
When you run the above command, It will ask you to enter the path for your private and public keys. Private key will be saved by “id_rsa” name and public key will be saved by “id_rsa.pub” name. By default the key will be saved in the following directory
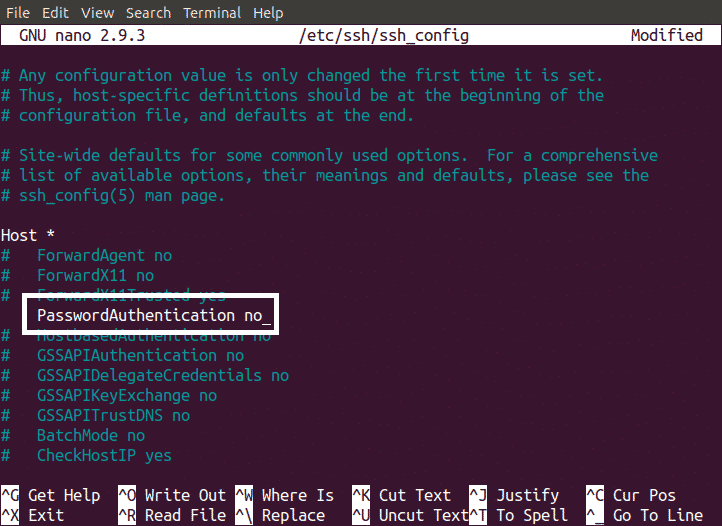
After creating public key use this key to configure SSH login with the key. After making sure that key is working to log into your SSH server, now disable password based log in. This can be done by editing our ssh_config file. Open the file in your desired editor. Now remove the # before “PasswordAuthentication yes” and replace it with
Now your SSH server can only be accessed by public key and access through password has been disabled
Allowing a Single IP to log in
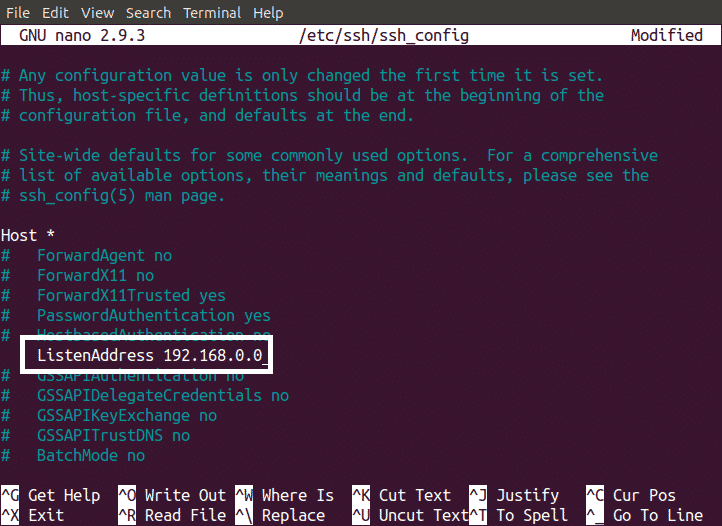
By default you can SSH into your server from any IP address. Server can be made more secure by allowing a single IP to access your server. This can be done by adding the following line in your ssh_config file.
This will block all the IP’s to log into your SSH server other than the Entered IP (i.e. 192.168.0.0).
NOTE: Enter the IP of your machine in place of “192.168.0.0”.
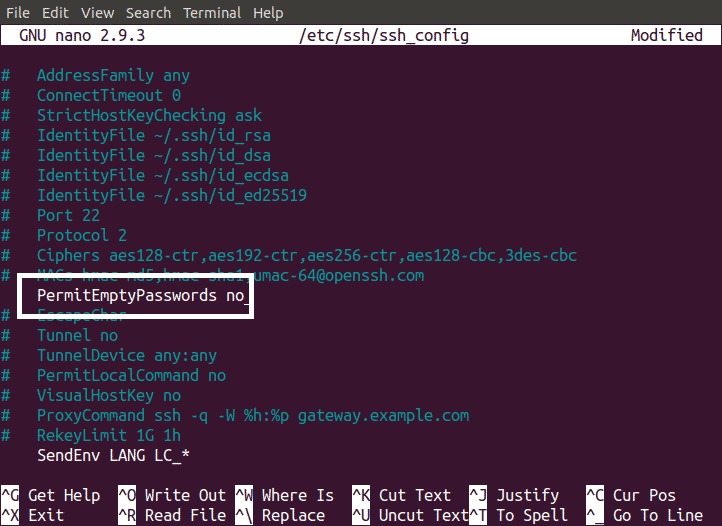
Disabling Empty Password
Never allow log into SSH Server with empty password. If empty password is allowed then your server is more likely to be attacked by brute force attackers. To disable Empty password login, open ssh_config file and make the following changes
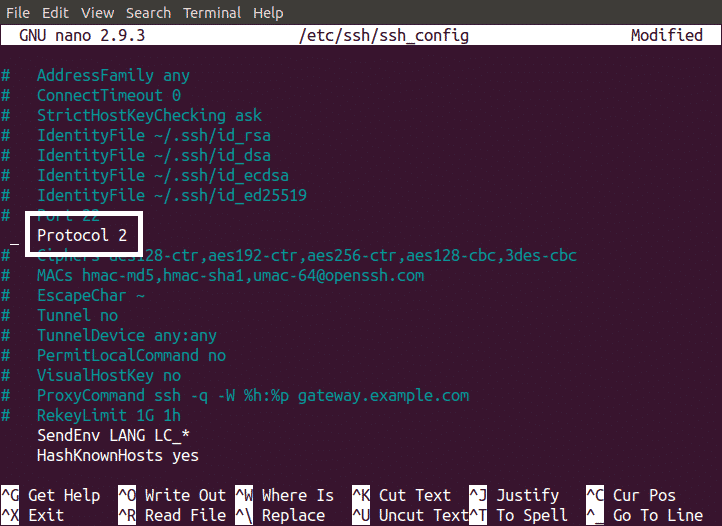
Using Protocol 2 for SSH Server
Previous protocol used for SSH is SSH 1. By default the protocol is set to SSH 2 but if it is not set to SSH 2, you must change it to SSH 2. SSH 1 protocol has some issues related to security and these issues have been fixed in SSH 2 protocol. To change it, edit ssh_config file as shown below
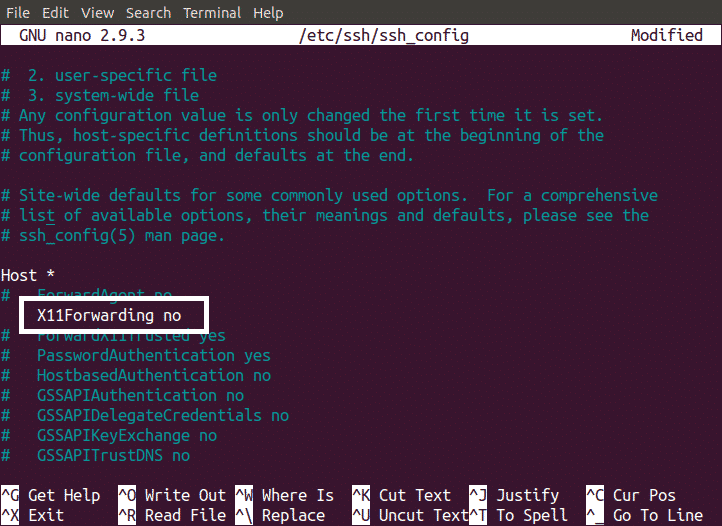
By Disabling X11 Forwarding
X11 Forwarding feature gives a Graphical User Interface (GUI) of your SSH server to the remote user. If X11 Forwarding is not disabled then any hacker, who has hacked your SSH session, can easily find all the data in your server. You can avoid this by disabling X11 Forwarding. This can be done by changing the ssh_config file as shown below
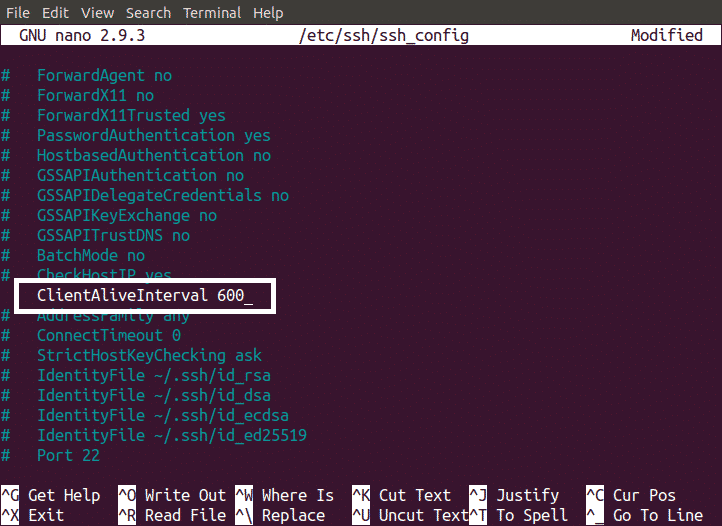
Setting an Idle Timeout
Idle timeout means, if you do not do any activity in your SSH server for a specific interval of time, you are automatically logged out from your server
We can enhance security measures for our SSH server by setting an idle timeout. For example you SSH your server and after some time you get busy doing some other tasks and forget to logout of your session. This is a very high security risk for your SSH server. This security issue can be overcome by setting an idle timeout. Idle timeout can be set by changing our ssh_config file as shown below
By setting idle timeout to 600, the SSH connection will be dropped after 600 seconds (10 minutes) of not any activity.
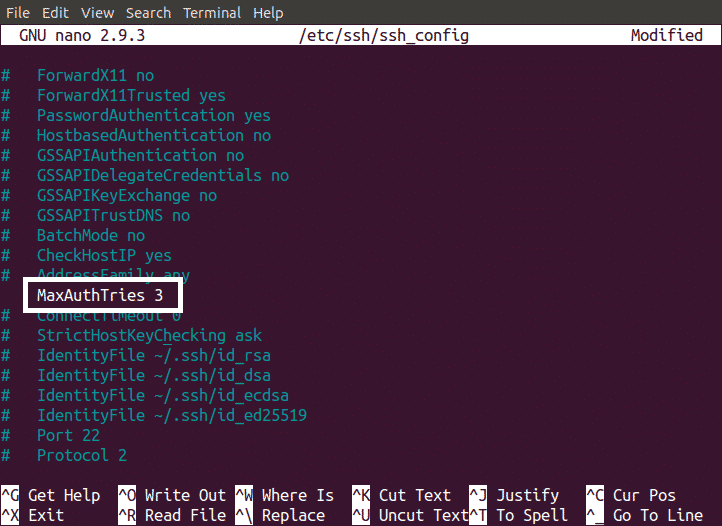
Setting a Limited Password Tries
We can also make our SSH server secure by setting a specific number of password tries. This is helpful against brute force attackers. We can set a limit for password tries by changing ssh_config file.
Restarting SSH Service
Many of the above methods need to restart SSH service after applying them. We can restart SSH service by typing the following command in the Terminal
Conclusion
After applying the above changes to your SSH server, now your server is much more secure than before and it is not easy for a brute force attacker to hack your SSH server.