Nmap is another example about the altruist community’s power leading the technological development. Today the variety of configurations or parameters we can apply to a scan allows us to directly detect vulnerabilities, while years ago by using Nmap we could only suppose and test. Currently the accuracy is a lot higher and we even can scan vulnerabilities with Nmap.
Nmap works by delivering packets to the target and analyzing its responses but before continuing to talk about Nmap let’s remind some basics about networking including the most popular protocols, ICMP, TCP and UDP.
Internet Control Message Protocol (ICMP)
It is a protocol mainly used to send information rather than transporting data. Usually used to report errors when a request is done, that’s why, just like TCP or UDP, ICMP must not be underestimated. Examples of ICMP are the famous PING which returns information about the destination IP or the TRACEROUTE command under Windows (Under Linux the “traceroute” command by default uses UDP). Of course, we can give additional uses to this protocol, if my memory does not fail, forcing ICMP connection was one of the ways to bypass routers web based security login.
Internet protocol suite (Known as TCP/IP)
This is the most popular protocol, or suite of protocols. Initially one protocol later divided into two: TCP and IP. While the IP protocol is responsible for identifying the destination address, TCP is responsible to make the delivery, when TCP delivers packets it informs the sender about it’s reception, it also notifies the sender in case of errors during the transportation.
We can compare the Internet Protocol (IP) as the guy who when we order a pizza answers the phone and writes all the data including what we order and our address, and TCP is the guy who takes the pizza on the motorcycle to our home, if the guy can’t find the customers’ address, he will call the pizzeria to report the problem.
User Datagram Protocol (Known as UDP)
UDP is similar to TCP with a basic difference: it does not care about the result. If a packet fails to reach its destination UDP won’t notify the sender about the problem.
NMAP installation
According to Nmap’s website we can download the RPM and convert it for use in different distribution packages but the truth is apt-get to install nmap works fine both for Ubuntu and Debian. First check if you have Nmap already installed. While we already saw on LinuxHint how to get a complete list of installed packages this time we will check specifically for the program by running the following command:
The console must return the route of the program, otherwise, it is not installed. We can also run the following command:
Here an example of the command outputs in case you have already Nmap installed.

If you haven’t got Nmap installed and are on Debian or Ubuntu just run:
For other distributions check normal mechanisms for your distribution of choice to find nmap.
Getting started with Nmap
First of all, lets run nmap with a target without parameters and check what we receive
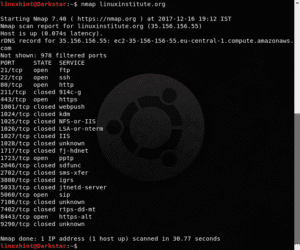
Without parameters, nmap already give us information about our target, we can see Linux Institute is hosted on Amazon, it’s external IP and what ports are open or closed.
To continue, lets clarify nmap quires root privileges in order to run some parameters, please do “su” and become root. Now we’ll run the following command in order to detect open services:
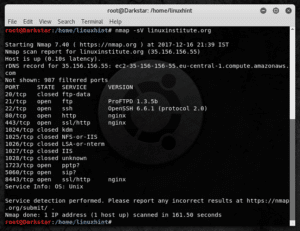
As we can see the host has the FTP, SSH and Nginx services running. The command even told us the versions of the programs which is useful if we are looking for vulnerabilities.
Now lets run the -O parameter in order to know the target’s Operating system:
(In contrast with commands ran above, this one was ran from a Windows version of nmap against itself)
Output:
Nmap scan report for localhost (127.0.0.1)
Host is up (0.029s latency).
Other addresses for localhost (not scanned): ::1
Not shown: 998 closed ports
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
Device type: general purpose|media device
Running (JUST GUESSING): Microsoft Windows Longhorn|10|2008|7|Vista|8.1 (93%), Microsoft embedded (88%)
OS CPE: cpe:/o:microsoft:windows cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_7::sp1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_8.1:r1 cpe:/h:microsoft:xbox_one
Aggressive OS guesses: Microsoft Windows Longhorn (93%), Microsoft Windows 10 build 15031 (92%), Microsoft Windows 10 build 10586 (91%), Microsoft Windows Server 2008 SP2 (91%), Microsoft Windows 7 SP1 (91%), Microsoft Windows 8.1 Update 1 (91%), Microsoft Windows 8 (91%), Microsoft Windows Vista SP1 (90%), Microsoft Windows 7 Enterprise SP1 (89%), Microsoft Windows 10 1511 (89%)No exact OS matches for host (test conditions non-ideal).
Network Distance: 0 hopsOS detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 6.64 seconds
We see the target system, in this case the localhost, is running Windows, the scanner fails to specify it’s version, which is 10, that’s why Nmap throws a percentage of accuracy.
By default scan is done with SYN when possible with parameter -sS, this procedure is the default because it tries to avoid detection by firewalls or IDS.
TCP parameter -sT tries to connect to each port leaving a log on the target system. You can check services using UDP protocols with by adding –sU parameter.
Additional details about port and service scanning can be found at https://nmap.org/book/man-port-scanning-techniques.html
And to see all parameters for Nmap please run “man nmap” in a terminal.
Advanced auditory with Nmap
Now lets see some more interesting scans. Nmap includes a suite of scripts (Nmap Scripting Engine, NSE) which may help us find security holes in our system.

Output:
NSE: Loaded 101 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 09:57
Completed NSE at 09:58, 10.00s elapsed
Initiating NSE at 09:58
Completed NSE at 09:58, 0.00s elapsed
Initiating Ping Scan at 09:58
Scanning www.hiddendomainname.info (X.X.X.X (Target IP)) [4 ports]
Completed Ping Scan at 09:58, 0.19s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:58
Completed Parallel DNS resolution of 1 host. at 09:58, 0.50s elapsed
Initiating SYN Stealth Scan at 09:58
Scanning www.hiddendomainname.info (X.X.X.X (Target IP)) [1000 ports]
Discovered open port 1723/tcp on X.X.X.X (Target IP)
Discovered open port 993/tcp on X.X.X.X (Target IP)
Discovered open port 443/tcp on X.X.X.X (Target IP)
Discovered open port 143/tcp on X.X.X.X (Target IP)
Discovered open port 21/tcp on X.X.X.X (Target IP)
Discovered open port 53/tcp on X.X.X.X (Target IP)
Discovered open port 110/tcp on X.X.X.X (Target IP)
Discovered open port 80/tcp on X.X.X.X (Target IP)
Discovered open port 25/tcp on X.X.X.X (Target IP)
Discovered open port 3306/tcp on X.X.X.X (Target IP)
Discovered open port 995/tcp on X.X.X.X (Target IP)
Discovered open port 22/tcp on X.X.X.X (Target IP)
Discovered open port 5060/tcp on X.X.X.X (Target IP)
Discovered open port 465/tcp on X.X.X.X (Target IP)
Discovered open port 106/tcp on X.X.X.X (Target IP)
Discovered open port 8443/tcp on X.X.X.X (Target IP)
Completed SYN Stealth Scan at 09:58, 13.28s elapsed (1000 total ports)
NSE: Script scanning X.X.X.X (Target IP).
Initiating NSE at 09:58
Completed NSE at 10:11, 793.83s elapsed
Initiating NSE at 10:11
Completed NSE at 10:11, 0.00s elapsed
Nmap scan report for www.hiddendomainname.info (X.X.X.X (Target IP))
Host is up (0.17s latency).
Not shown: 984 closed ports
PORT STATE SERVICE
21/tcp open ftp
|_sslv2-drown:
22/tcp open ssh
25/tcp open smtp
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: postfix builtin
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
53/tcp open domain
80/tcp open http
|_http-csrf: Couldn’t find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn’t find any DOM based XSS.
| http-enum:
|_ /robots.txt: Robots file
|_http-stored-xss: Couldn’t find any stored XSS vulnerabilities.
106/tcp open pop3pw
110/tcp open pop3
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
143/tcp open imap
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
443/tcp open https
| http-cookie-flags:
| /:
| PHPSESSID:
| secure flag not set and HTTPS in use
|_ httponly flag not set
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=www.hiddendomainname.info
| Found the following possible CSRF vulnerabilities:
|
| Path: https://www.hiddendomainname.info:443/
| Form id: main-contact-form
| Form action: /contact
|
| Path: https://www.hiddendomainname.info/#
| Form id: main-contact-form
| Form action: /contact
|
| Path: https://www.hiddendomainname.info/#services
| Form id: main-contact-form
| Form action: /contact
|
| Path: https://www.hiddendomainname.info/#contact
| Form id: main-contact-form
| Form action: /contact
|
| Path: https://www.hiddendomainname.info/
| Form id: main-contact-form
| Form action: /contact
|
| Path: https://www.hiddendomainname.info/user/login/
| Form id: login
| Form action: /user/login
|
| Path: https://www.hiddendomainname.info/#about-us
| Form id: main-contact-form
| Form action: /contact
|
| Path: https://www.hiddendomainname.info/user/login
| Form id: login
|_ Form action: /user/login
|_http-dombased-xss: Couldn’t find any DOM based XSS.
| http-enum:
| /blog/: Blog
| /login/: Login page
| /robots.txt: Robots file
| /blog/wp-login.php: WordPress login page.
| /index/: Potentially interesting folder
| /page/: Potentially interesting folder
| /upload/: Potentially interesting folder
|_ /webstat/: Potentially interesting folder (401 Unauthorized)
| http-fileupload-exploiter:
|
| Couldn’t find a file-type field.
|
| Couldn’t find a file-type field.
|
| Couldn’t find a file-type field.
|
| Couldn’t find a file-type field.
|
| Couldn’t find a file-type field.
|
|_ Couldn’t find a file-type field.
|_http-stored-xss: Couldn’t find any stored XSS vulnerabilities.
|_sslv2-drown:
465/tcp open smtps
| smtp-vuln-cve2010-4344:
|_ The SMTP server is not Exim: NOT VULNERABLE
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: postfix builtin
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
993/tcp open imaps
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
995/tcp open pop3s
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
| Modulus Type: Safe prime
| Modulus Source: Unknown/Custom-generated
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
1723/tcp open pptp
3306/tcp open mysql
5060/tcp open sip
8443/tcp open https-alt
| http-enum:
| /admin/: Possible admin folder
| /admin/admin/: Possible admin folder
| /administrator/: Possible admin folder
| /adminarea/: Possible admin folder
| /adminLogin/: Possible admin folder
| /admin_area/: Possible admin folder
| /administratorlogin/: Possible admin folder
| /admin/index.html: Possible admin folder
| /admin/login.html: Possible admin folder
| /admin/admin.html: Possible admin folder
| /admin_area/login.html: Possible admin folder
| /admin_area/index.html: Possible admin folder
| /admincp/: Possible admin folder
| /admincp/index.asp: Possible admin folder
| /admincp/index.html: Possible admin folder
| /admin/account.html: Possible admin folder
| /adminpanel.html: Possible admin folder
| /admin/admin_login.html: Possible admin folder
| /admin_login.html: Possible admin folder
| /admin_area/admin.html: Possible admin folder
| /admin/home.html: Possible admin folder
| /admin/admin-login.html: Possible admin folder
| /admin-login.html: Possible admin folder
| /admin/adminLogin.html: Possible admin folder
| /adminLogin.html: Possible admin folder
| /adminarea/index.html: Possible admin folder
| /adminarea/admin.html: Possible admin folder
| /admin/controlpanel.html: Possible admin folder
| /admin.html: Possible admin folder
| /admin/cp.html: Possible admin folder
| /administrator/index.html: Possible admin folder
| /administrator/login.html: Possible admin folder
| /administrator/account.html: Possible admin folder
| /administrator.html: Possible admin folder
| /adminarea/login.html: Possible admin folder
| /admincontrol/login.html: Possible admin folder
| /admincontrol.html: Possible admin folder
| /admin/account.cfm: Possible admin folder
| /admin/index.cfm: Possible admin folder
| /admin/login.cfm: Possible admin folder
| /admin/admin.cfm: Possible admin folder
| /admin.cfm: Possible admin folder
| /admin/admin_login.cfm: Possible admin folder
| /admin_login.cfm: Possible admin folder
| /adminpanel.cfm: Possible admin folder
| /admin/controlpanel.cfm: Possible admin folder
| /admincontrol.cfm: Possible admin folder
| /admin/cp.cfm: Possible admin folder
| /admincp/index.cfm: Possible admin folder
| /admincp/login.cfm: Possible admin folder
| /admin_area/admin.cfm: Possible admin folder
| /admin_area/login.cfm: Possible admin folder
| /administrator/login.cfm: Possible admin folder
| /administratorlogin.cfm: Possible admin folder
| /administrator.cfm: Possible admin folder
| /administrator/account.cfm: Possible admin folder
| /adminLogin.cfm: Possible admin folder
| /admin2/index.cfm: Possible admin folder
| /admin_area/index.cfm: Possible admin folder
| /admin2/login.cfm: Possible admin folder
| /admincontrol/login.cfm: Possible admin folder
| /administrator/index.cfm: Possible admin folder
| /adminarea/login.cfm: Possible admin folder
| /adminarea/admin.cfm: Possible admin folder
| /adminarea/index.cfm: Possible admin folder
| /admin/adminLogin.cfm: Possible admin folder
| /admin-login.cfm: Possible admin folder
| /admin/admin-login.cfm: Possible admin folder
| /admin/home.cfm: Possible admin folder
| /admin/account.asp: Possible admin folder
| /admin/index.asp: Possible admin folder
| /admin/login.asp: Possible admin folder
| /admin/admin.asp: Possible admin folder
| /admin_area/admin.asp: Possible admin folder
| /admin_area/login.asp: Possible admin folder
| /admin_area/index.asp: Possible admin folder
| /admin/home.asp: Possible admin folder
| /admin/controlpanel.asp: Possible admin folder
| /admin.asp: Possible admin folder
| /admin/admin-login.asp: Possible admin folder
| /admin-login.asp: Possible admin folder
| /admin/cp.asp: Possible admin folder
| /administrator/account.asp: Possible admin folder
| /administrator.asp: Possible admin folder
| /administrator/login.asp: Possible admin folder
| /admincp/login.asp: Possible admin folder
| /admincontrol.asp: Possible admin folder
| /adminpanel.asp: Possible admin folder
| /admin/admin_login.asp: Possible admin folder
| /admin_login.asp: Possible admin folder
| /adminLogin.asp: Possible admin folder
| /admin/adminLogin.asp: Possible admin folder
| /adminarea/index.asp: Possible admin folder
| /adminarea/admin.asp: Possible admin folder
| /adminarea/login.asp: Possible admin folder
| /administrator/index.asp: Possible admin folder
| /admincontrol/login.asp: Possible admin folder
| /admin2.asp: Possible admin folder
| /admin2/login.asp: Possible admin folder
| /admin2/index.asp: Possible admin folder
| /administratorlogin.asp: Possible admin folder
| /admin/account.aspx: Possible admin folder
| /admin/index.aspx: Possible admin folder
| /admin/login.aspx: Possible admin folder
| /admin/admin.aspx: Possible admin folder
| /admin_area/admin.aspx: Possible admin folder
| /admin_area/login.aspx: Possible admin folder
| /admin_area/index.aspx: Possible admin folder
| /admin/home.aspx: Possible admin folder
| /admin/controlpanel.aspx: Possible admin folder
| /admin.aspx: Possible admin folder
| /admin/admin-login.aspx: Possible admin folder
| /admin-login.aspx: Possible admin folder
| /admin/cp.aspx: Possible admin folder
| /administrator/account.aspx: Possible admin folder
| /administrator.aspx: Possible admin folder
| /administrator/login.aspx: Possible admin folder
| /admincp/index.aspx: Possible admin folder
| /admincp/login.aspx: Possible admin folder
| /admincontrol.aspx: Possible admin folder
| /adminpanel.aspx: Possible admin folder
| /admin/admin_login.aspx: Possible admin folder
| /admin_login.aspx: Possible admin folder
| /adminLogin.aspx: Possible admin folder
| /admin/adminLogin.aspx: Possible admin folder
| /adminarea/index.aspx: Possible admin folder
| /adminarea/admin.aspx: Possible admin folder
| /adminarea/login.aspx: Possible admin folder
| /administrator/index.aspx: Possible admin folder
| /admincontrol/login.aspx: Possible admin folder
| /admin2.aspx: Possible admin folder
| /admin2/login.aspx: Possible admin folder
| /admin2/index.aspx: Possible admin folder
| /administratorlogin.aspx: Possible admin folder
| /admin/index.jsp: Possible admin folder
| /admin/login.jsp: Possible admin folder
| /admin/admin.jsp: Possible admin folder
| /admin_area/admin.jsp: Possible admin folder
| /admin_area/login.jsp: Possible admin folder
| /admin_area/index.jsp: Possible admin folder
| /admin/home.jsp: Possible admin folder
| /admin/controlpanel.jsp: Possible admin folder
| /admin.jsp: Possible admin folder
| /admin/admin-login.jsp: Possible admin folder
| /admin-login.jsp: Possible admin folder
| /admin/cp.jsp: Possible admin folder
| /administrator/account.jsp: Possible admin folder
| /administrator.jsp: Possible admin folder
| /administrator/login.jsp: Possible admin folder
| /admincp/index.jsp: Possible admin folder
| /admincp/login.jsp: Possible admin folder
| /admincontrol.jsp: Possible admin folder
| /admin/account.jsp: Possible admin folder
| /adminpanel.jsp: Possible admin folder
| /admin/admin_login.jsp: Possible admin folder
| /admin_login.jsp: Possible admin folder
| /adminLogin.jsp: Possible admin folder
| /admin/adminLogin.jsp: Possible admin folder
| /adminarea/index.jsp: Possible admin folder
| /adminarea/admin.jsp: Possible admin folder
| /adminarea/login.jsp: Possible admin folder
| /administrator/index.jsp: Possible admin folder
| /admincontrol/login.jsp: Possible admin folder
| /admin2.jsp: Possible admin folder
| /admin2/login.jsp: Possible admin folder
| /admin2/index.jsp: Possible admin folder
| /administratorlogin.jsp: Possible admin folder
| /administr8.asp: Possible admin folder
| /administr8.jsp: Possible admin folder
| /administr8.aspx: Possible admin folder
| /administr8.cfm: Possible admin folder
| /administr8/: Possible admin folder
| /administer/: Possible admin folder
| /administracao.asp: Possible admin folder
| /administracao.aspx: Possible admin folder
| /administracao.cfm: Possible admin folder
| /administracao.jsp: Possible admin folder
| /administracion.asp: Possible admin folder
| /administracion.aspx: Possible admin folder
| /administracion.jsp: Possible admin folder
| /administracion.cfm: Possible admin folder
| /administrators/: Possible admin folder
| /adminpro/: Possible admin folder
| /admins/: Possible admin folder
| /admins.cfm: Possible admin folder
| /admins.jsp: Possible admin folder
| /admins.asp: Possible admin folder
| /admins.aspx: Possible admin folder
| /administracion-sistema/: Possible admin folder
| /admin108/: Possible admin folder
| /admin_cp.asp: Possible admin folder
| /admin/backup/: Possible backup
| /admin/download/backup.sql: Possible database backup
| /admin/CiscoAdmin.jhtml: Cisco Collaboration Server
| /admin-console/: JBoss Console
| /admin4.nsf: Lotus Domino
| /admin5.nsf: Lotus Domino
| /admin.nsf: Lotus Domino
| /smbcfg.nsf: Lotus Domino
| /admin/view/javascript/fckeditor/editor/filemanager/connectors/test.html:</pre>
<pre>OpenCart/FCKeditor File upload
| /admin/includes/FCKeditor/editor/filemanager/upload/test.html:</pre>
<pre>ASP Simple Blog / FCKeditor File Upload
| /admin/jscript/upload.html: Lizard Cart/Remote File upload
| /admin/jscript/upload.pl: Lizard Cart/Remote File upload
| /admin/jscript/upload.asp: Lizard Cart/Remote File upload
|_ /admin/environment.xml: Moodle files
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| ssl-dh-params:
| VULNERABLE:
| Diffie-Hellman Key Exchange Insufficient Group Strength
| State: VULNERABLE
| Transport Layer Security (TLS) services that use Diffie-Hellman groups
| of insufficient strength, especially those using one of a few commonly
| shared groups, may be susceptible to passive eavesdropping attacks.
| Check results:
| WEAK DH GROUP 1
| Cipher Suite: TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
| Modulus Type: Safe prime
| Modulus Source: nginx/1024-bit MODP group with safe prime modulus
| Modulus Length: 1024
| Generator Length: 8
| Public Key Length: 1024
| References:
|_ https://weakdh.org
|_sslv2-drown:
NSE: Script Post-scanning.
Initiating NSE at 10:11
Completed NSE at 10:11, 0.00s elapsed
Initiating NSE at 10:11
Completed NSE at 10:11, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 818.50 seconds
Raw packets sent: 1166 (51.280KB) | Rcvd: 1003 (40.188KB)
As we can see from the above output, Nmap found many vulnerabilities, I ran the scan against a weak unattended application. We see from broken ssl cipher to access to very sensitive files and folders belonging to the admin. When you get “cve-xxx” (Common Vulnerabilities Exposures) results you can search on exploit databases.
DOS Vulnerability Diagnostic
DOS is among the easiest attacks to carry out, lets check with Nmap if our host is vulnerable to DOS attacks by running the following command:
The option -v is for verbosity, otherwise we may wait too much time without knowing what is going on.
You can find other scripts to run with nmap besides, besides the dos script at this link: https://nmap.org/nsedoc/index.html
In this tutorial I showed you various ways to diagnose vulnerabilities with nmap and this should get you started on your way.


