Installing Nikto:
In this case I’m using a Debian system, you can download Nikto for Debian at https://packages.debian.org/jessie/all/nikto/download . In case your system returns dependency errors when executing “dpkg -i <packagename>” (as explained at https://linuxhint.com/uninstall-debian-packages/) execute the command “apt –fix-broken install” and you’ll get it installed.
Getting started with Nikto:
Like with any Linux package you can always throw a “man nikto” to learn all parameters. The first parameter we’ll use, and which is mandatory, is -host (or -h)to specify the target. In this case I decided to use as target a very old unmaintained website which may throw interesting results:
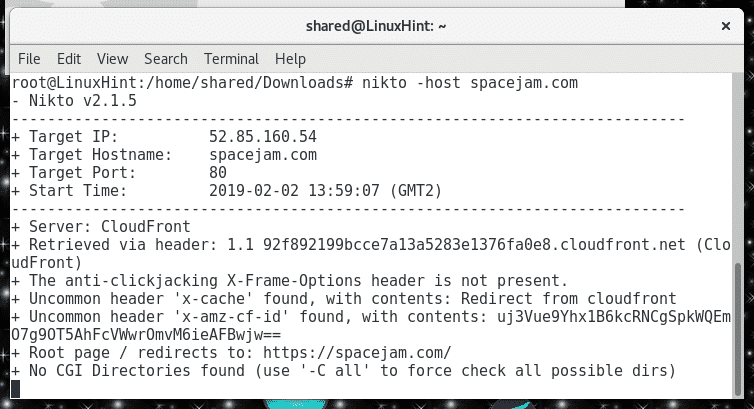
As with any scanner we receive basic information useful in a footprinting process but additionally we can see within the first results Nikto already discovered a possible vulnerability exposing the website to Clickjacking attacks.
After seeing Nikto’s recommendation to add the “-C all” parameter, I stopped the scanning, you can restart including -C all.
CGI (Common Gateway Interface) is a way through which Web Servers interact with software or programs installed on the server.
In this case we weren’t lucky but as shown above, Nikto successfully found a possible vulnerability despite the website has not CGI content, take in consideration vulnerabilities may be false positive therefore not exploitable.
Let’s check a different target, www.telered.com.ar , an Internet provider website:

The website has no redirection to www so I launched the scan again.
You can see they are using an old Apache version under CentOS and several possible vulnerabilities like OSVDB-877, OSVDB-3092, OSVDB-3268, OSVDB-3233, in the past we could search in the http://www.osvdb.org database but it is offline now, therefore we’ll need to base the vulnerability on the information Nikto provides or to google it, in this case we would google Cross Site Tracing attacks.
Let’s combine Nikto with Nmap, so we can see what ports a Webserver has open before using Nikto, ill throw a basic Nmap scan against the same target to check if it has additional ports open.
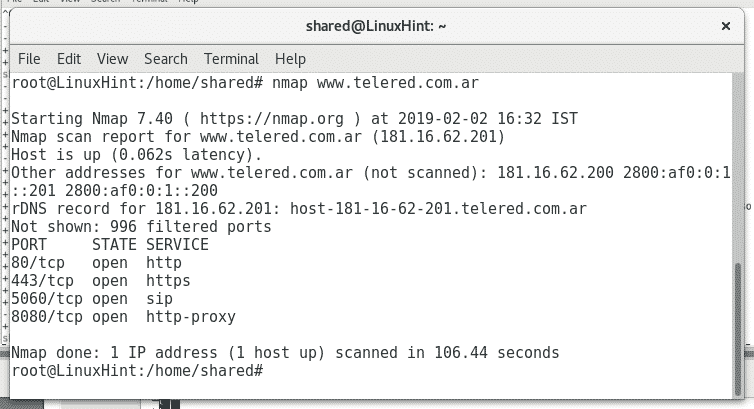
The interesting here may be the port 5060 used for VOIP, the port seems associated with known vulnerabilities according to this source, through Nikto it is unlikely to give important results but let’s try it.
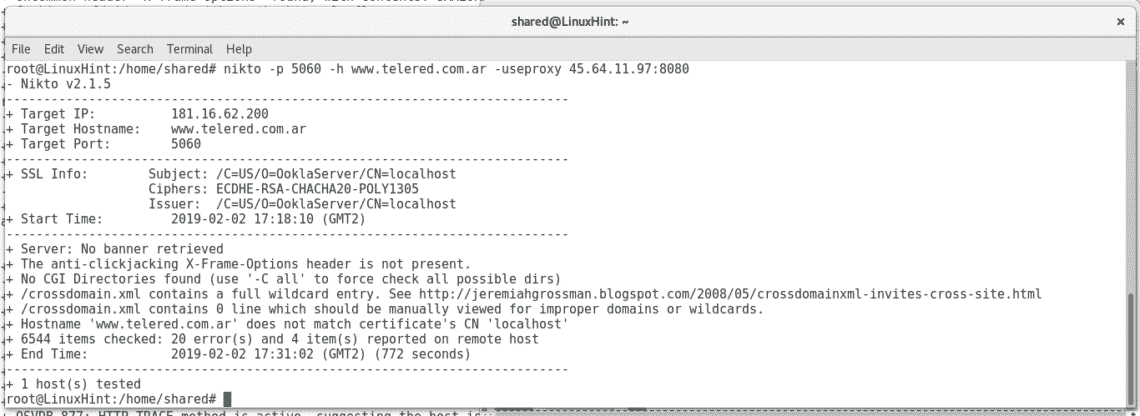
Where
-p = specifies the port.
-h = specifies the host
-useproxy = to scan using a proxy and avoid the target to see our IP.
In contrast with the scan we launched before now Nikto found a XML file linking us to a blog article explaining the vulnerability the file may represent. It is recommendable to run Nmap against a target before using Nikto to target open ports.
It is important to highlight Nikto results will differ according to the parameters and data we use, even against the same target, for example, if you use the target’s domain name or the target’s IP or change the port. Let’s see if we can find a third different result on the same target:
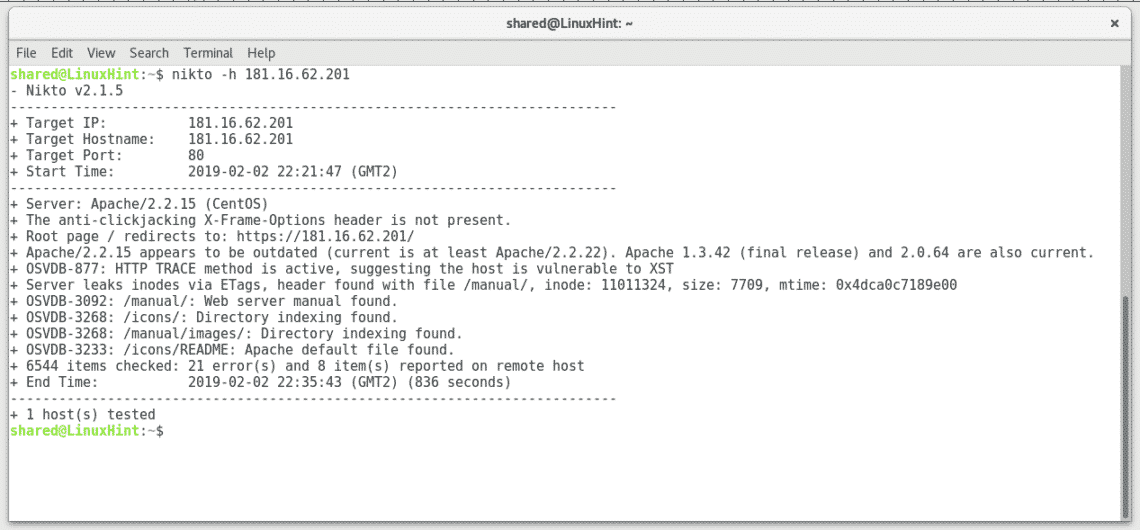
The result is very similar in this case, despite more errors were reported (21 vs 18 the first scan), possibly due redirection issues.
Multiple port scanning with Nikto:
If we run Nmap to discover a site has multiple ports open we can scan all them in a single Nikto session by separating ports with coma as shown below:
I run:
nikto -h proz.com -p 80,111,443,5666
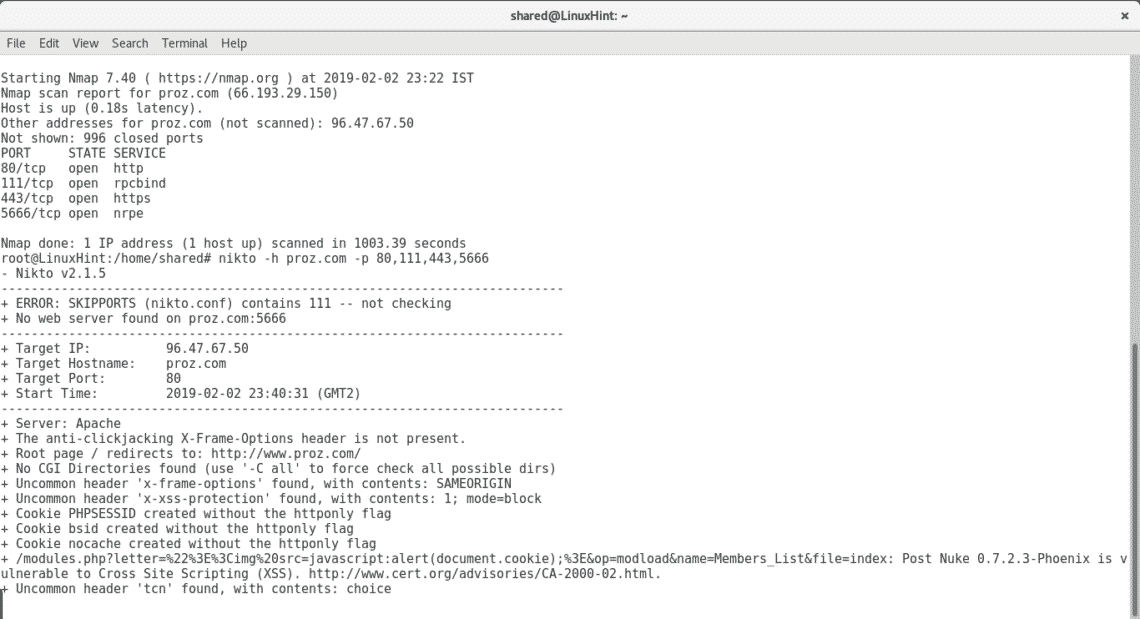
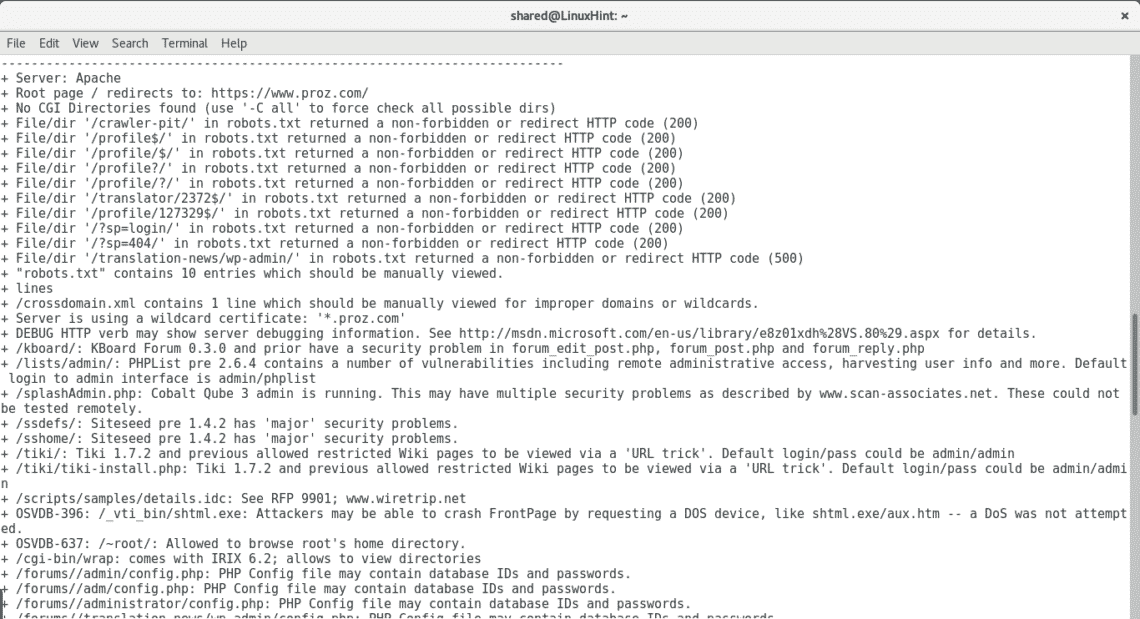
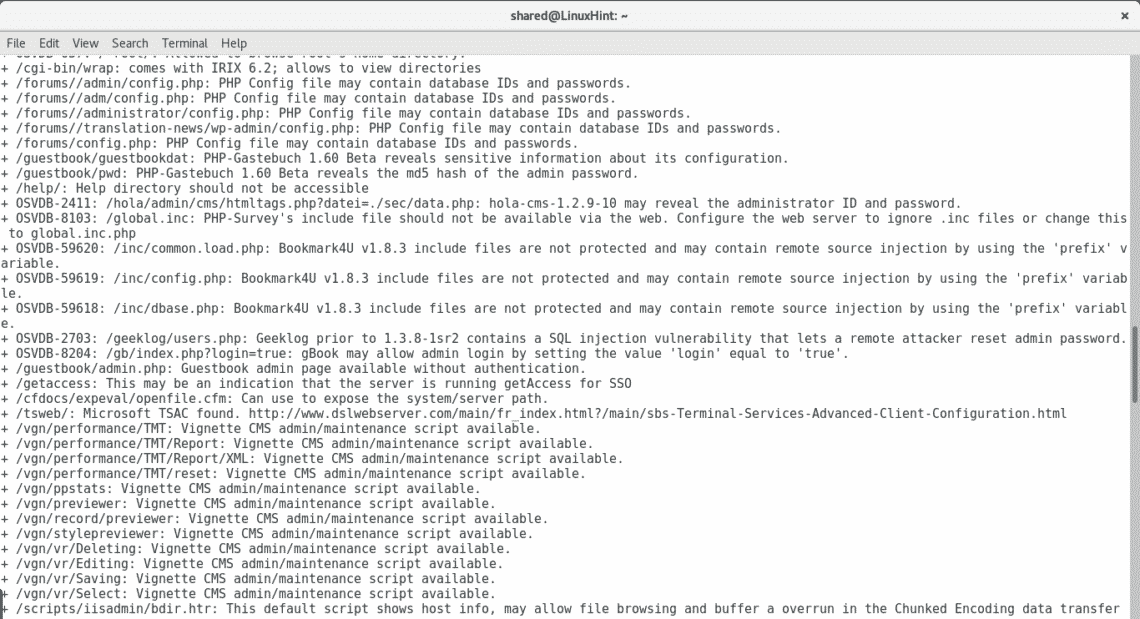


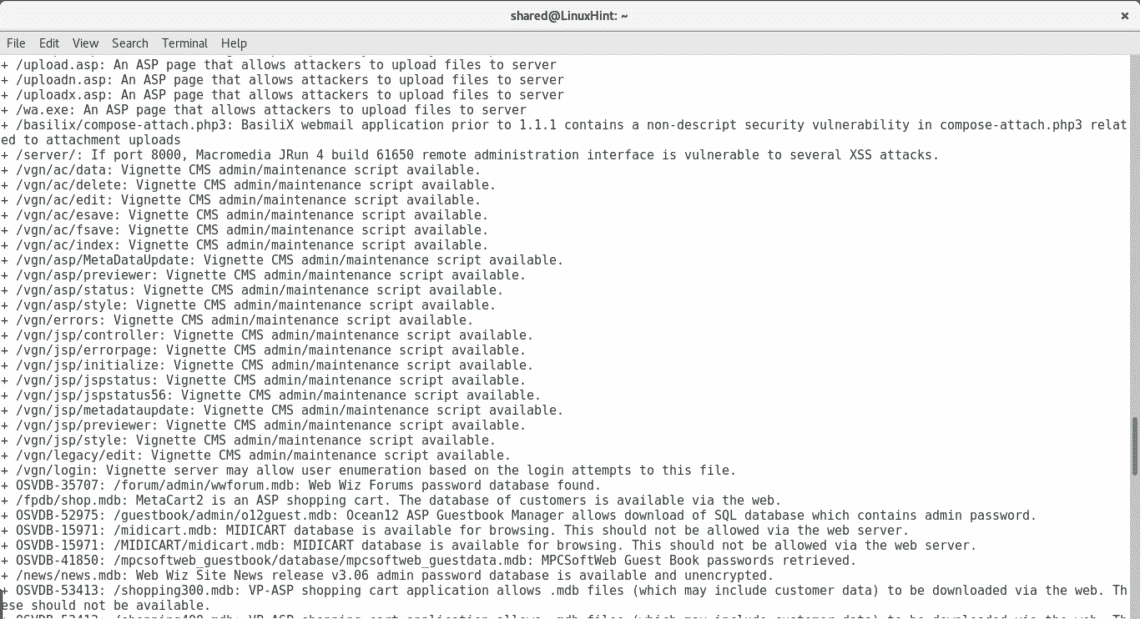
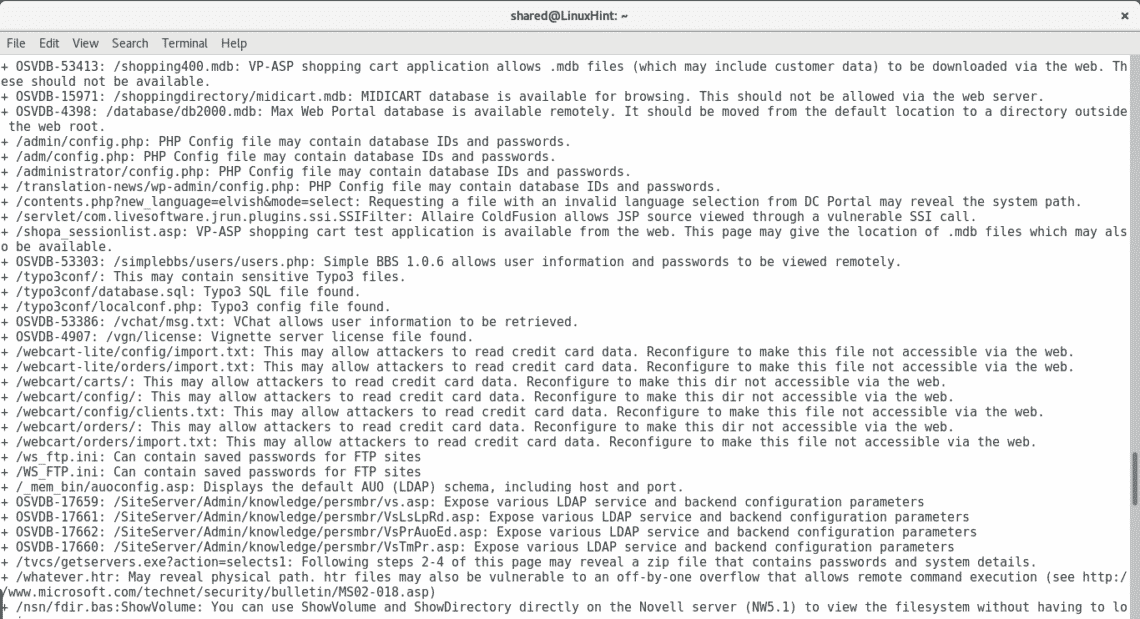
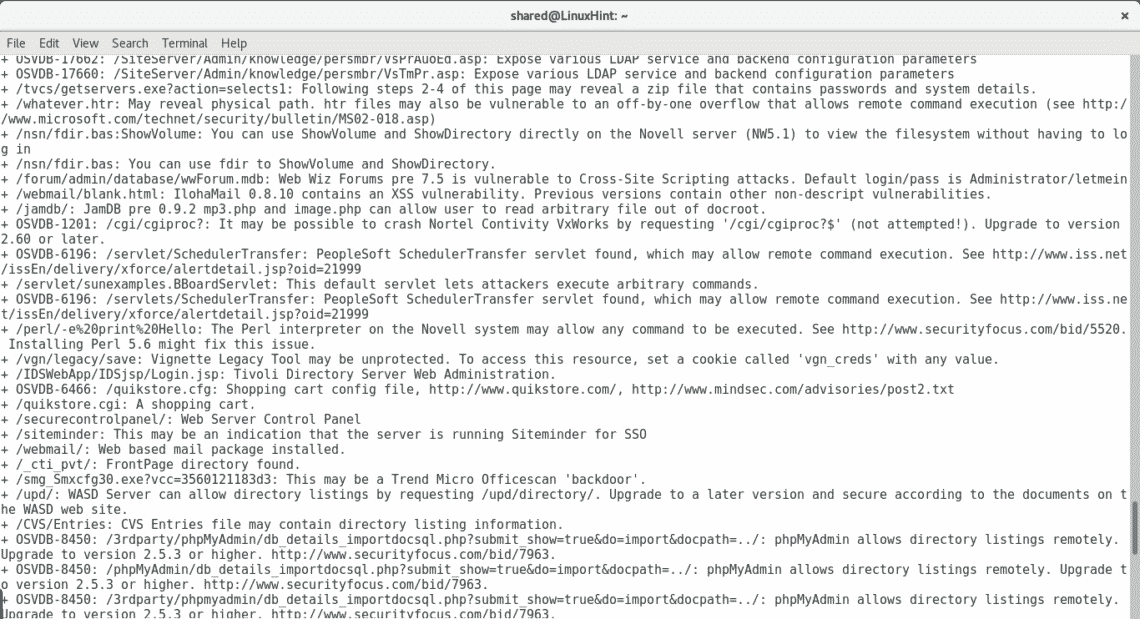
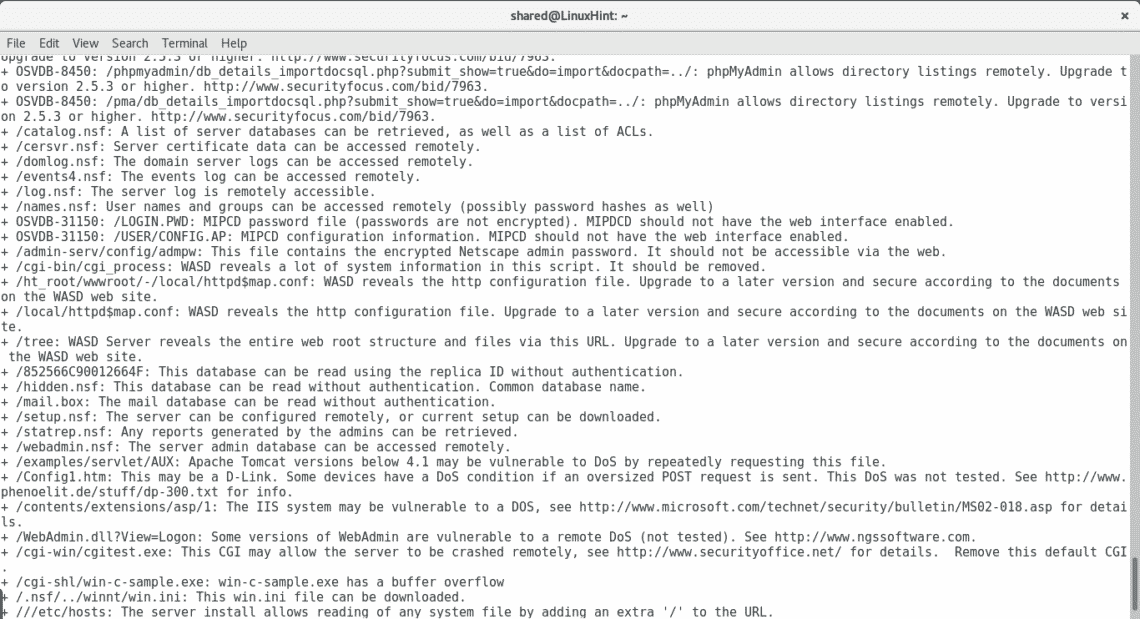
As you see after getting all open ports by Nmap I threw a Nikto scan, it automatically discards ports which are not running web applications. By adding all ports Nikto discovered multiple vulnerabilities including very sensitive directories holding possible credentials, SQL Injection and XSS vulnerabilities, brute force possibilities among a lot more of opportunities to exploit the server.
To reproduce Nikto results with complete results just run:
Using Nikto plugins:
“Nikto -list-plugins” will display a list of additional plugins which may help to scan a target or confirm a vulnerability reported by Nikto.
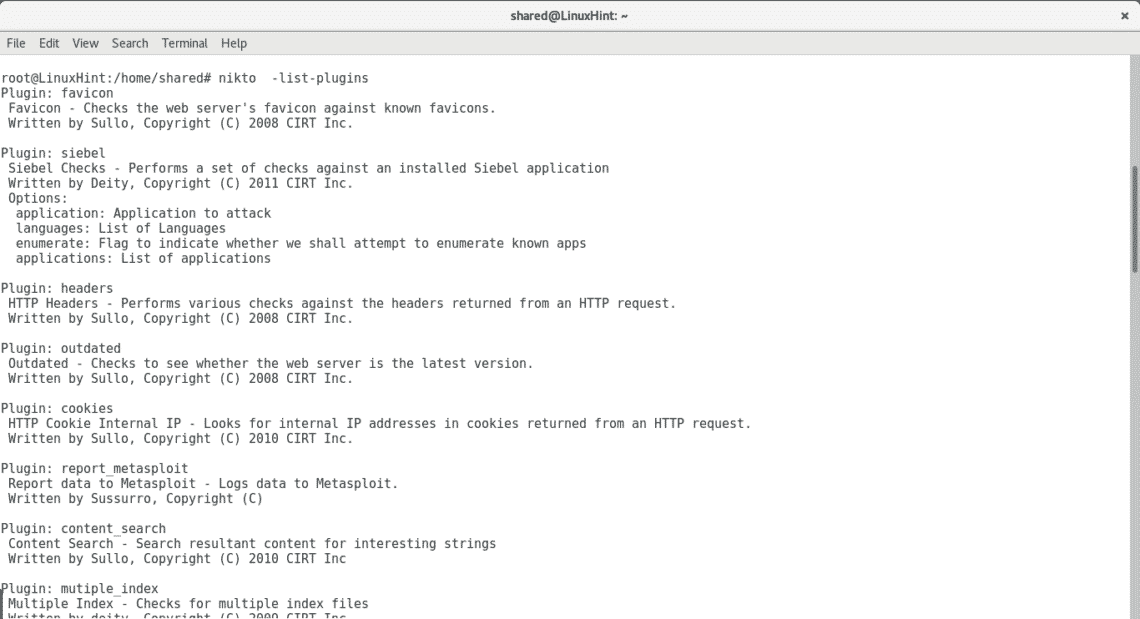
Let’s verify if the results above showing XSS vulnerabilities are not a false positive.
Run:
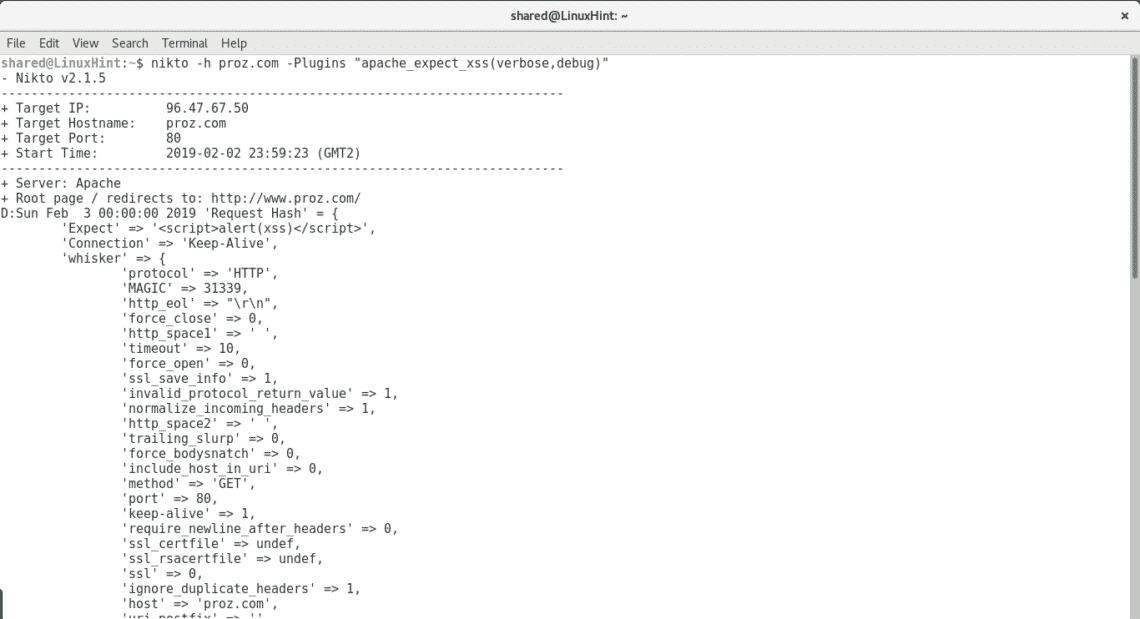
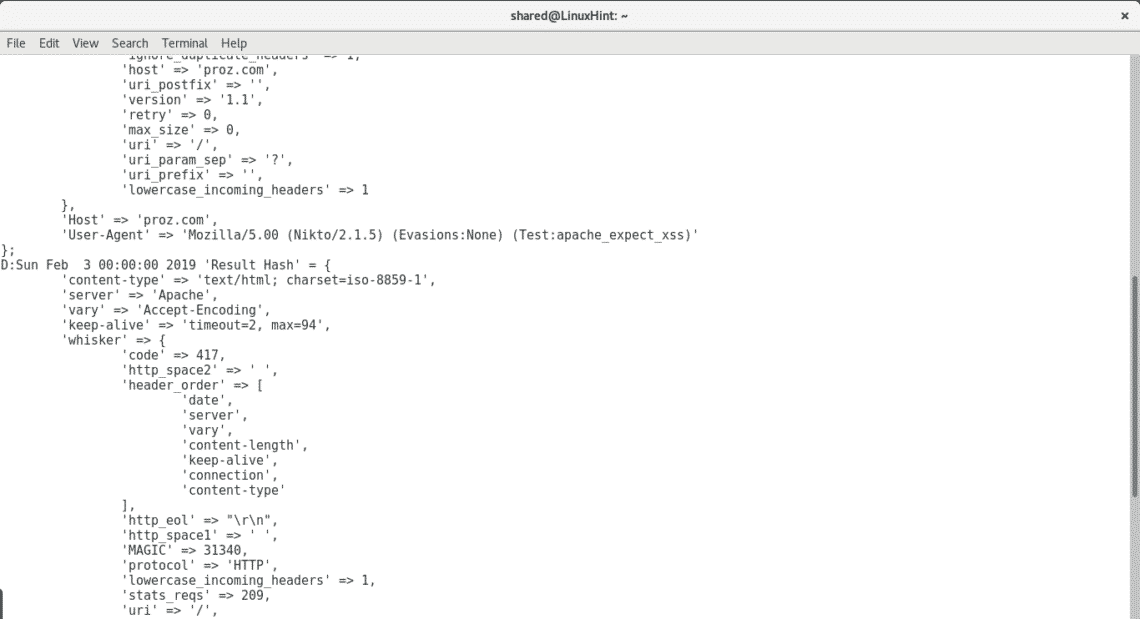
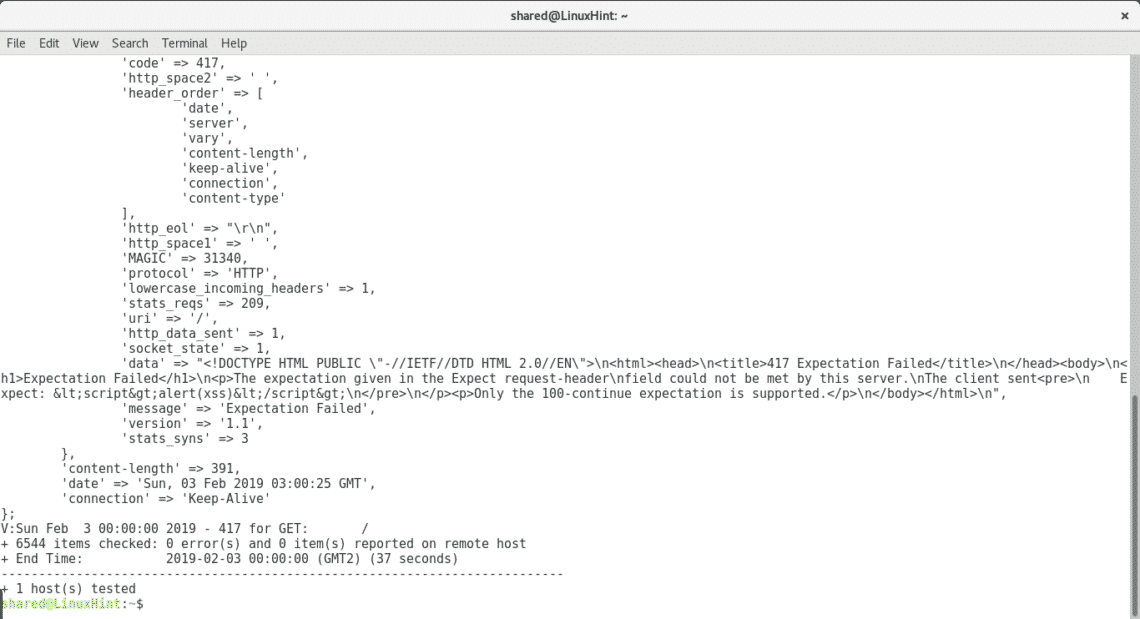
As we see in this case Nikto informs “‘message’ => ‘Expectation Failed” discarding the XSS vulnerability, if it was your server you could use different plugins to discard or confirm the rest of vulnerabilities.
Conclusion:
Nikto is a very light vulnerabilities scanner for web servers, it is useful if you have no time to deal with heavy scanners like Nexpose or Nessus, despite this, if you have time to analyze your target I would recommend a more complete scanner like Nexpose, Nessus, OpenVAS or Nmap, some of which we already analyzed at LinuxHint simply because they are not limited to web servers and all aspects deserve to be deeply checked in order to protect a server.


