Contrary to these Intrusion Detection Systems (Usually referred as IDS), Advanced Intrusion Detection Environment (Known as AIDE) checks for files integrity by comparing the system files information and attributes with a database initially created.
First it creates the database of the healthy system to later compare the integrity using algorithms sha1, rmd160, tiger, crc32, sha256, sha512, whirlpool with optional integrations for gost, haval and cr32b. Of course AIDE supports remote monitoring.
Together with files information AIDE checks for files attributes such as file type, permissions, GID, UID, size, link name, block count, number of links, mtime, ctime and atime and attributes generated by XAttrs, SELinux, Posix ACL and Extended. With AIDE it is possible to specify files and directories to be excluded or included in monitoring tasks.
Setup and configure: Install Advanced Intrusion Detection Environment on Debian
To start by installing AIDE on Debian and derived Linux distributions run:
After installing AIDE, the first step to follow is to create a database on your health system to be contrasted with snapshots to verify files integrity.
To build the initial database run:
Note: if you had a previous database AIDE will overwrite it (prior confirmation request), it is recommended to do a verification before proceeding.
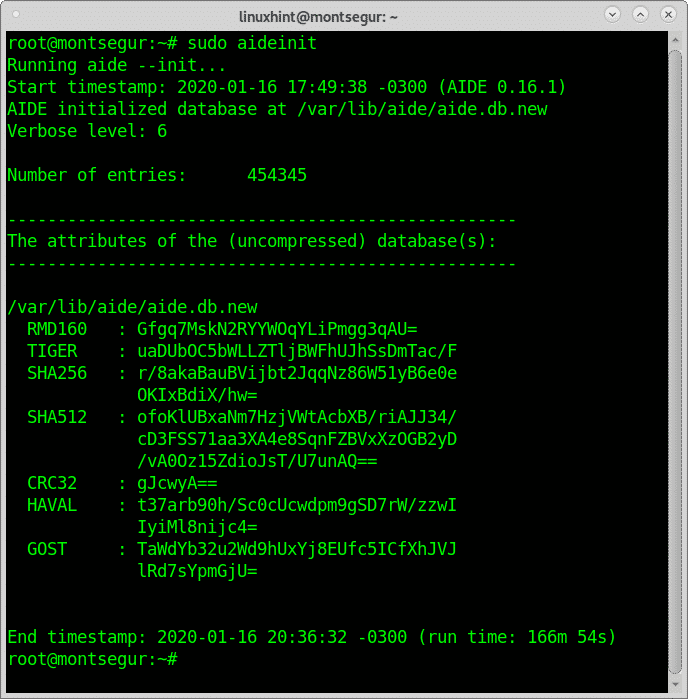
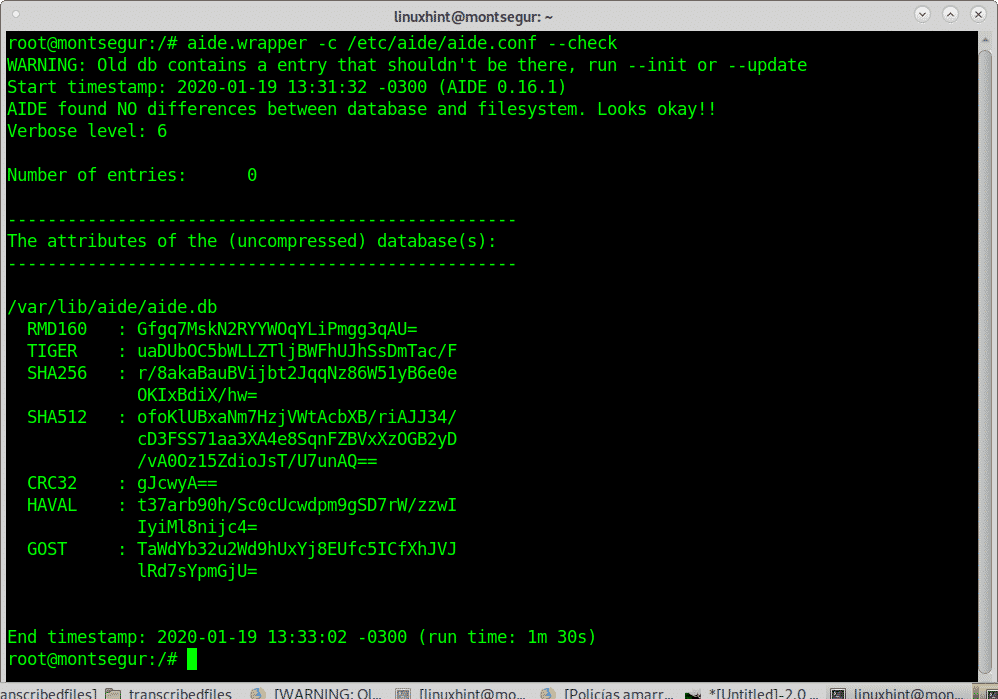
This process may last long minutes until showing the output you can see below
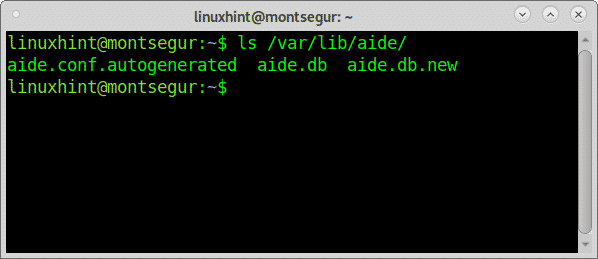
As you can see the database was generated at /var/lib/aide/aide.db.new, within the directory /var/lib/aide/ you’ll also see a file called aide.db:
If the output is 0 AIDE did not find problems. If the flag –check is applied then the possible outputs meaning are:
1 = New files were found in the system.
2 = Files were removed from the system.
4 = Files in the system suffered changes.
14 = Error writing error.
15 = Invalid argument error.
16 = Unimplemented function error.
17 = Invalid configureline error.
18 = I/O error.
19 = Version mismatch error.
AIDE options and parameters include:
–init or -i: this option initializes the database, this is a mandatory execution prior to any check, checks won’t work if the database wasn’t initialized first.
–check or -C: when applied this option AIDE compares the system files with the database information. This is the default option applied when AIDE is executed without options.
–update or -u: this option is used to update a database.
–compare: this option is used to compare different databases, databases must be previously defined in the configuration file.
–config-check or -D: this option is useful to find errors in the configuration file, by adding this command AIDE will only read the configuration without continuing the process with files checking.
–config or -c = this parameter is useful to specify other configuration file than aide.conf.
–before or -B = add configuration parameters before reading the configuration file.
–after or -A = add configuration parameters after reading the configuration file.
–verbose or -V = with this command you can specify the verbosity level which can be defined between 0 and 255.
–report or -r = with this option you can send AIDE’s results report to other destinations, you can repeat this option instructing AIDE to send reports to different destinations.
You can get additional information on these and more AIDE commands and options in the man page.
AIDE Configuration File:
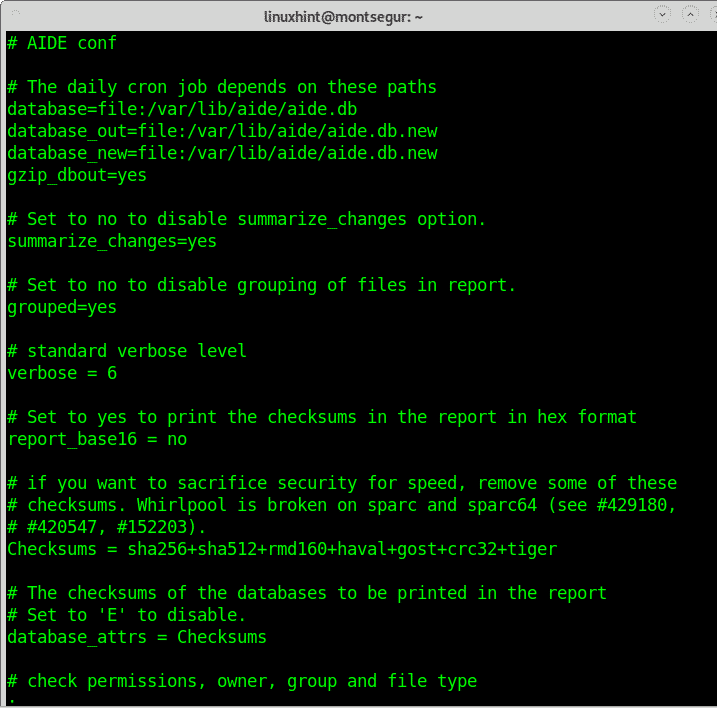
AIDE’s configuration is done on the configuration file located within /etc/aide.conf, from there you can define AIDE’s behavior, below you have some of the most popular options explained:
The lines in the configuration file include, among more functionalities:
database_out: here you can specify the new db location. While you can define several destinations when launching the command, in this configuration file you can set only one url.
database_new: source db url when comparing databases.
database_attrs: Checksum
database_add_metadata: add additional information as comments such as db time creation,etc.
verbose: here you can input a value between 0 and 255 to define the verbosity level.
report_url: url defining output location.
report_quiet: skips output if no differences were found.
gzip_dbout: here you can define if the db should be compressed (depends on zlib).
warn_dead_symlinks: define if dead symlinks should be reported or not.
grouped: group files which reportedly suffered changes.
More instructions on the configuration file options are available at https://linux.die.net/man/5/aide.conf.
I hope you found this article on Setup And Configure Debian Linux Install Advanced Intrusion Detection Environment useful. Keep following LinuxHint for more tips and updates on Linux and networking.