What is ICMP ?
ICMP or Internet Control Message Protocol is Internet or Network layer protocol. In general it is used to check the reachability of a host or router in a network.
Who uses ICMP?
Ping or traceroute uses ICMP as inner protocol. Ping uses ICMP echo request and ICMP echo reply messages to check whether destination host is reachable or not.
Types of ICMP packet?
In general two types of ICMP packet
- ICMP echo request messages.
- ICMP echo reply messages.
How to get ICMP packet in Wireshark?
Step1: We can use ping tool to get ICMP request and reply.
Step2: Open command line or terminal in Windows or Linux respectively.
Step3: Run Wireshark.
Step4: Run below command
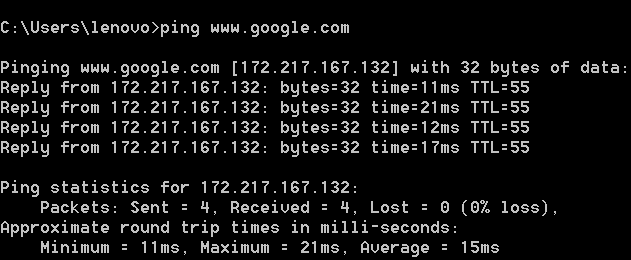
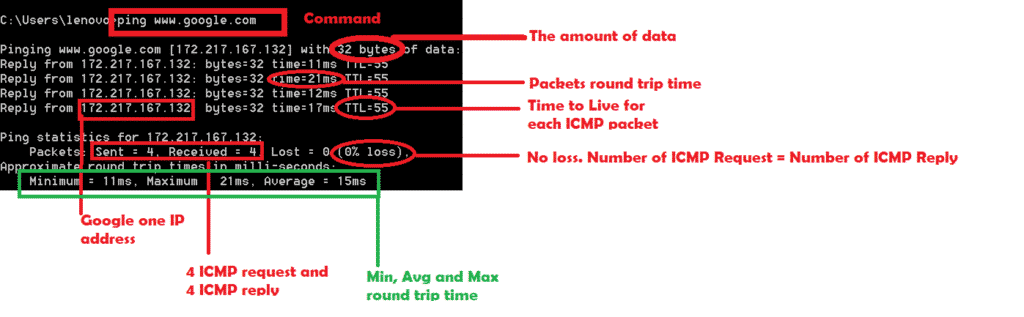
Make sure you have internet connection or ping will be failedJ. Here is the snapshot for successful ping to Google. We can see 0% loss. That means ICMP request packets = ICMP reply packets.
Here are the more details:
In this case we ping to Google web site. Instead we can do ping to ip address also.
OR
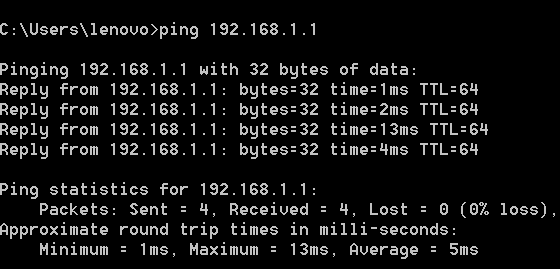
ping 192.168.1.1 [This is my router IP address]
Here is successful ping to my router
Step5: Stop Wireshark and put “ICMP” as filter in Wireshark.
Analysis on ICMP:
Let’s check what happens in Wireshark when we ping to Google or 192.168.1.1.
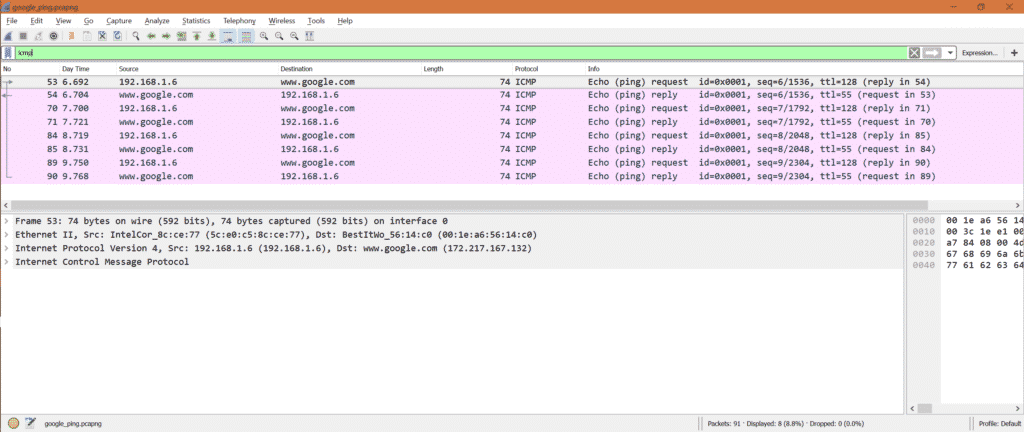
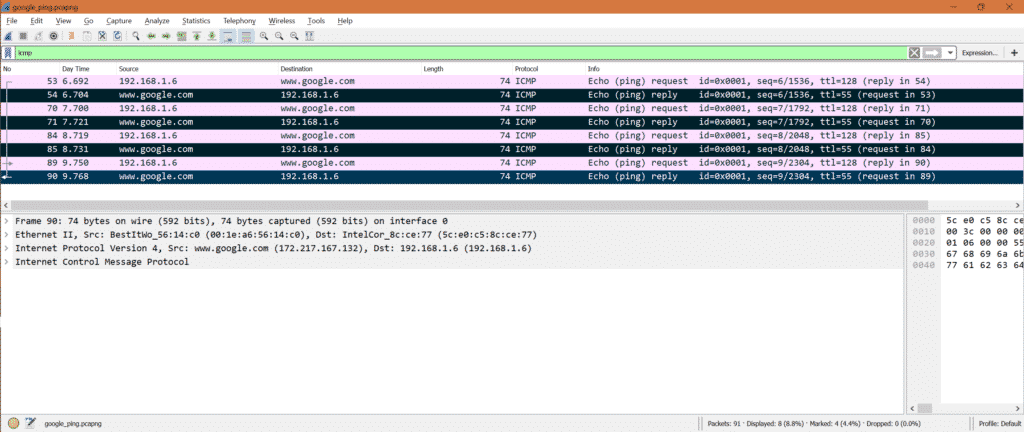
Here is the ICMP request and reply packets for Google ping.
Note: We have to put filter ‘icmp’ as we are interested only in ICMP packets.
Number of ICMP request: From capture we can see there are 4 ICMP request packets.
Check the marked packets.
Number of ICMP reply: From capture we can see there are 4 ICMP reply packets.
Check the marked packets.
ICMP Request:
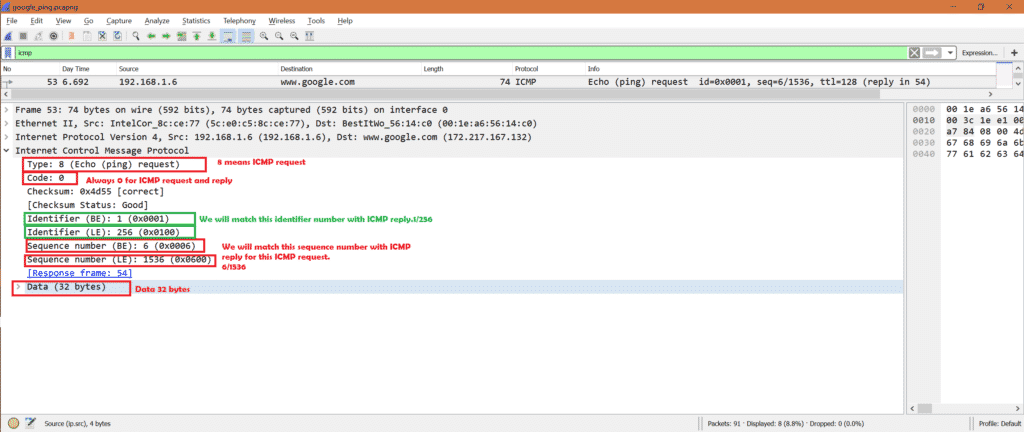
Now select ICMP request packet in Wireshark and look into IPv4 layer.
As this is ICMP request packet so we can see source IP as my system IP address and destination IP as Google’s one IP address. Also IP layer mentioned the protocol as ICMP.
Here is the screenshot
Now for the same packet select ICMP part in Wireshark.
We can see below important fields:
Code: 0 [Always 0 for ICMP packets]
Identifier (BE): 1
Identifier (LE): 256
Sequence Number (BE): 6
Sequence Number (LE): 1536
*BE –> Big Endian
*LE –> Little Endian
Data –> Data present in ICMP packet.
Here is the screenshot
ICMP Reply:
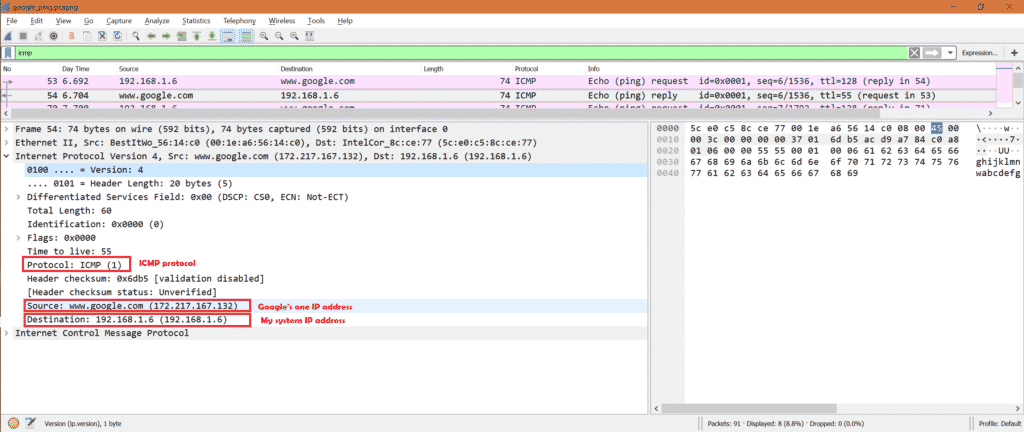
Now select ICMP reply packet in Wireshark and look into IPv4 layer.
As this is ICMP reply packet so we can see destination IP as my system IP address and source IP as Google’s one IP address. Also IP layer mentioned the protocol as ICMP.
Here is the screenshot
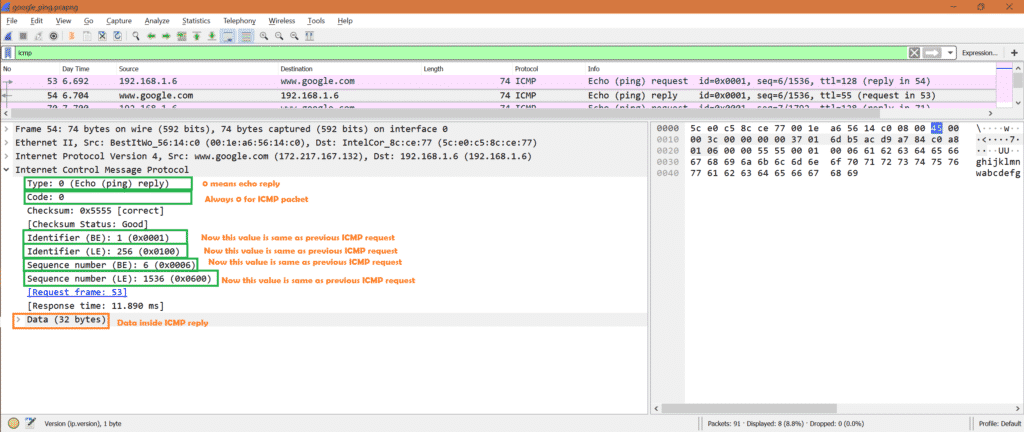
Now for the same packet select ICMP part in Wireshark.
We can see below important fields:
Code: 0 [Always 0 for ICMP packets]
Identifier (BE): 1
Identifier (LE): 256
Sequence Number (BE): 6
Sequence Number (LE): 1536
*BE –> Big Endian
*LE –> Little Endian
Data –> Data present in ICMP packet.
Here is the screenshot
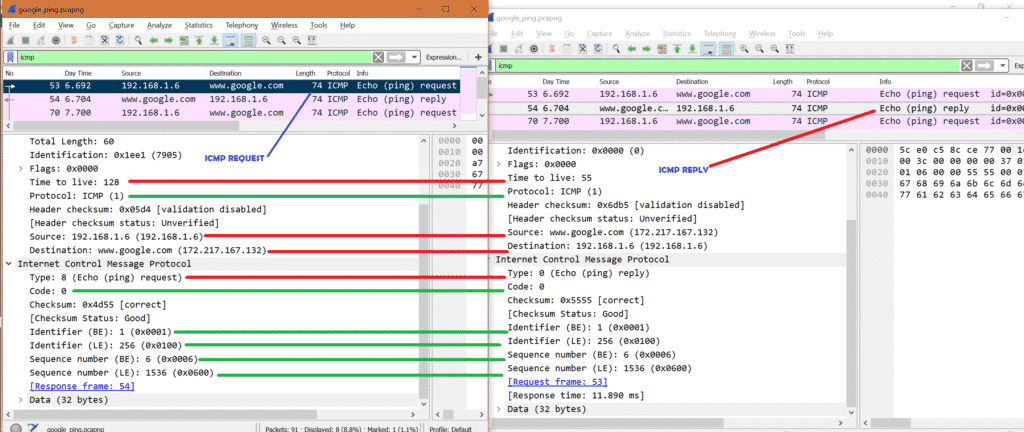
Now let’s see ICMP request and ICMP reply side by side in a picture.
*Red means it’s different
*Green means it’s same.
Special observation:
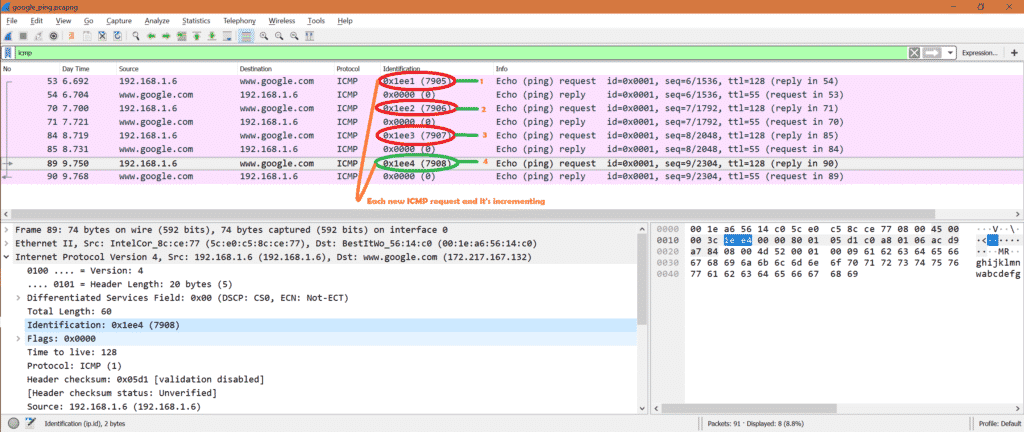
Let’s look into the Identification field inside IPv4 .We will see something interesting.
What happens if IP address is not reqachable:
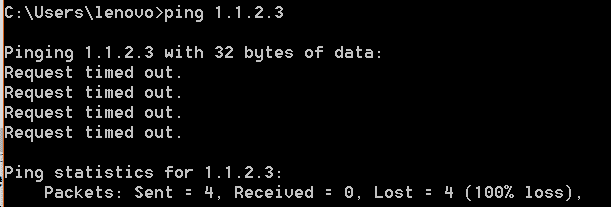
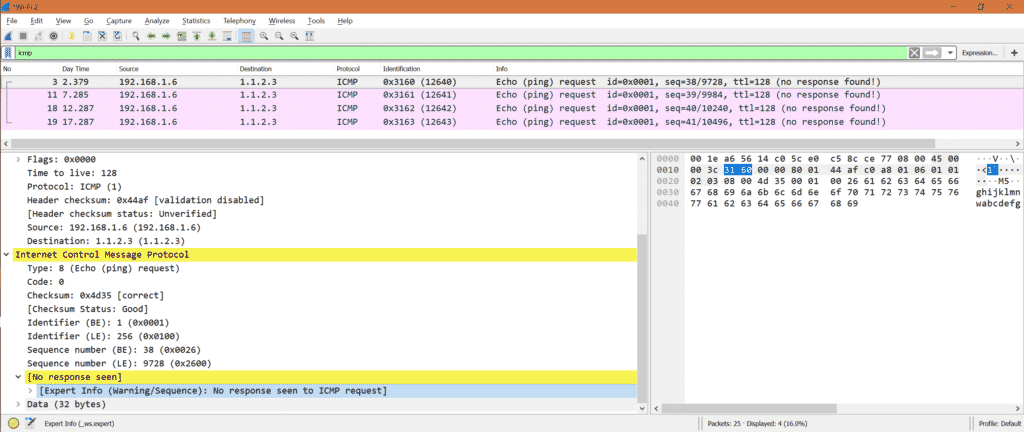
Let’s ping some ip address which is not accessible. So we will see below output.
Here is the snapshot for Wireshark
That means we did not receive any ICMP reply for any ICMP request.
Simple Conclusion:
So if we want to check any IP or website is reachable or not, we can use ping or traceroute which internally use ICMP protocol.
Quick Reference:
If interested to know other types of ICMP, follow below link
https://en.wikipedia.org/wiki/Internet_Control_Message_Protocol