In this tutorial Snort alert modes will be explained to instruct Snort to report over incidents in 5 different ways (ignoring the “no alert” mode), fast, full, console, cmg and unsock.
If you didn’t read the articles mentioned above and you don’t have previous experience with snort please get started with the tutorial on Snort installation and usage and continue with the article on rules before continuing this lecture. This tutorial assumes you have Snort already running.
To being let’s state Snort has 6 alert modes:
Fast: in this mode Snort will report the timestamp, alert message, IP source address and port and destination IP address and port. (-A fast)
Full: additionally to the fast mode alert, the full mode includes: TTL, IP packet and IP header length, service, ICMP type and sequence number. (-A full)
Console: prints fast alerts in the console. (-A console)
Cmg: This format was developed by Snort for testing purposes, it prints a full alert on the console without saving reports on logs. (-A cmg)
Unsock: export report to other programs through Unix Socket. (-A unsock)
None: Snort won’t generate alerts. (-A none)
All alert modes are preceded by a -A which is the parameter for alerts. Alerts are saved in the log /var/log/snort/alert. Snort default rules are capable to detect irregular activity such as port scanning. Let’s test each alert mode:
Fast alert test:
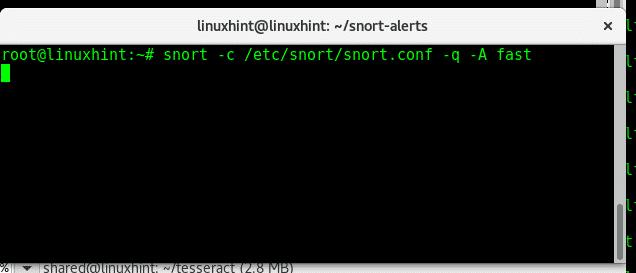
Where:
snort= calls the program
-c= path to config file, in this case the default one (/etc/snort/snort.conf)
-q= prevents snort from displaying initial information
-A= defines the alert mode, in this case fast.
While from a different computer I started an nmap scan against top 1000 ports alerts started to get logged to /var/log/snort/alert.

Full alert test:
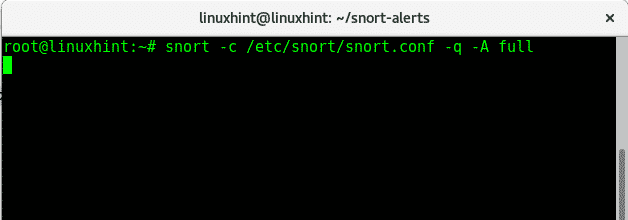
Where:
snort= calls the program
-c= path to config file, in this case the default one (/etc/snort/snort.conf)
-q= prevents snort from displaying initial information
-A= defines the alert mode, in this case full.
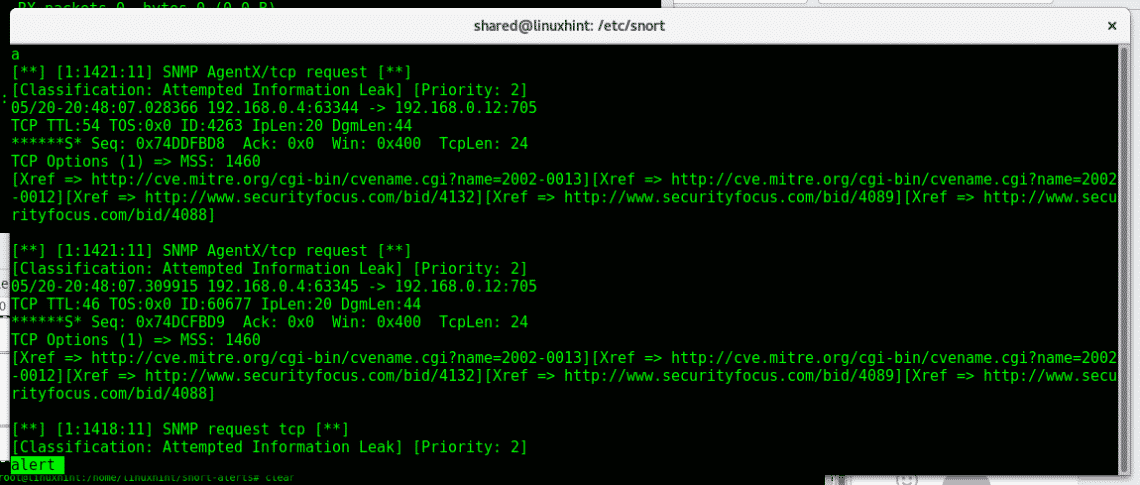
As you see the report gives additional information to the fast one.
Console alert test:
With the console alert test we’ll get alerts printed in the console, for this run

Where:
snort= calls the program
-c= path to config file, in this case the default one (/etc/snort/snort.conf)
-q= prevents snort from displaying initial information
-A= defines the alert mode, in this case console.
As you see the printed information is closer to a fast alert than a full one.
Cmg alert test:
Now let’s get a report in the console with the information of a full report and more. This mode was developed for testing purposes and does not log results.

Where:
snort= calls the program
-c= path to config file, in this case the default one (/etc/snort/snort.conf)
-q= prevents snort from displaying initial information
-A= defines the alert mode, in this case cmg.
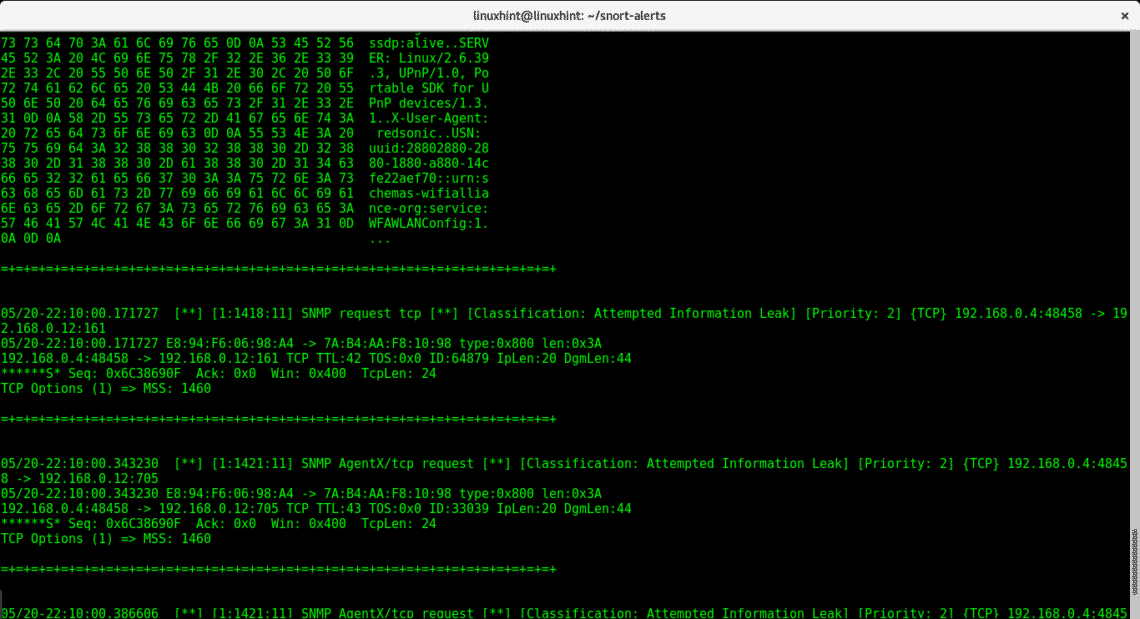
For the unsock alert to work, you’ll need to integrate it to a third party program or plugin.
Snort’s default alert mode is the full mode, if you don’t need the additional information of a fast, then a fast mode would increase the performance.
I hope this tutorial helped to understand Snort’s alert modes.


